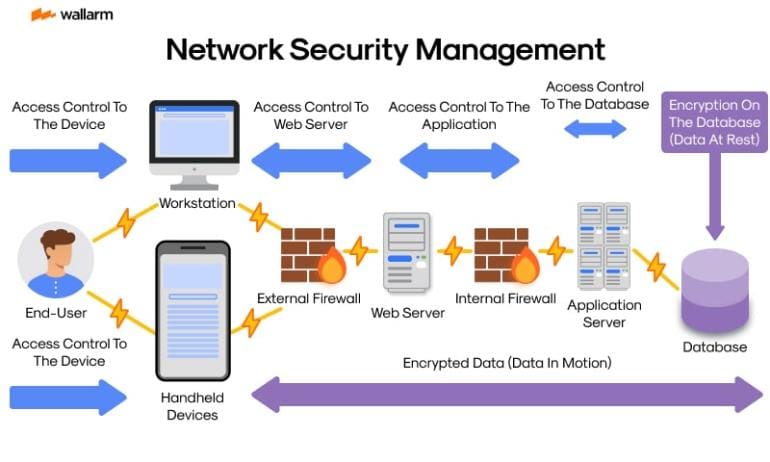
Network Security Management safeguards, verifies and facilitates uninterrupted data connectivity in digital space. It uses a range of tools, such as firewalls, antivirus suites and encryption mechanisms, to protect from internal and external threats. The management process also covers threat alertness, user authorisation and legal compliance. Network security policies are constantly reviewed and updated to fortify systems from potential risks, including sophisticated hacking attempts.

Top 10 Best Dynamic Application Security Testing (DAST) Platforms in 2025
Dynamic Application Security Testing (DAST) platforms have become fundamental for safeguarding web applications as digital assets and attack surfaces scale in both size and complexity.