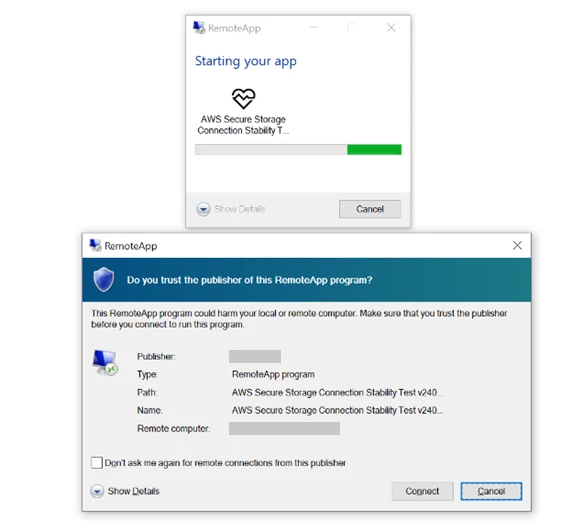
Russia-linked advanced persistent threat (APT), Midnight Blizzard, has launched a large-scale spear-phishing campaign, targeting over 1,000 users across more than 100 organizations. Noted for its involvement in past high-profile hacks, the group is said to be using signed RDP configuration files to gain access to targeted devices, thereby extending local system resources to their server. Entities in government, defense, academia, NGO, and other sectors have been targeted, with victims being found in the UK, Europe, Australia, and Japan.

Cyber expert speaks on Winston-Salem cyber incident – WFMYNews2.com
A cyber expert provided insight and analysis on a cyber incident in Winston-Salem in a report on WFMYNews2.com. The article likely discussed the details of