Researchers discovered a significant software supply chain vulnerability in a recently acquired subsidiary, earning a $50,500 bounty from a corporate bug bounty program. The ethical hackers exploited mismanaged Docker images containing proprietary code and exposed tokens, highlighting the risks of overlooked assets during acquisitions and the importance of securing software supply chains. The vulnerability demonstrated potential widespread impact on development and production environments.
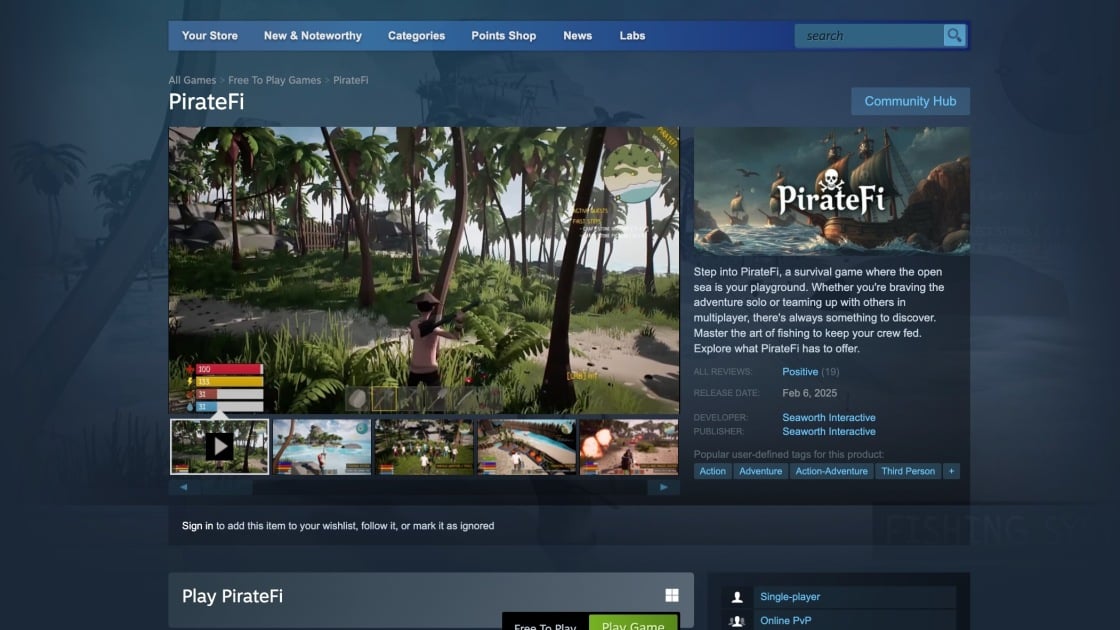
Did You Download This Steam Game? Sorry, It’s Windows Malware
A hacker published a free-to-play game, PirateFi, on gaming platform Steam with the aim of infecting users’ PC with Windows-based malware. The malware, noted as