Hey San Francisco Bay Area folks! I’m sure you’ve already heard about the recent high-profile cyberattacks on MGM Resorts and Caesar Entertainment. As both fellow members of this tech city and a cybersecurity enthusiast—like yours truly—I thought we could dive deep into what happened and draw some relevant lessons.
MGM Resorts got hit by a crippling ransomware attack in September. If you think that’s harsh, they’re not alone. Just three days before, Ceasar Entertainment fell prey to a similar attack, coughing up a whopping 15 to 30 million dollars as ransom.
Turns out, the attack on MGM Resorts was severe, with rumblings of an estimated $80 million in lost revenue, along with more than 36 hours of IT downtime. Talk about a nightmare! The service disruptions affected everyone from regular visitors to high-rollers, demonstrating just how pervasive and destructive such an attack can be.
Around a week and a half after the attack, MGM announced that operations were back to normal. But let’s break it down.
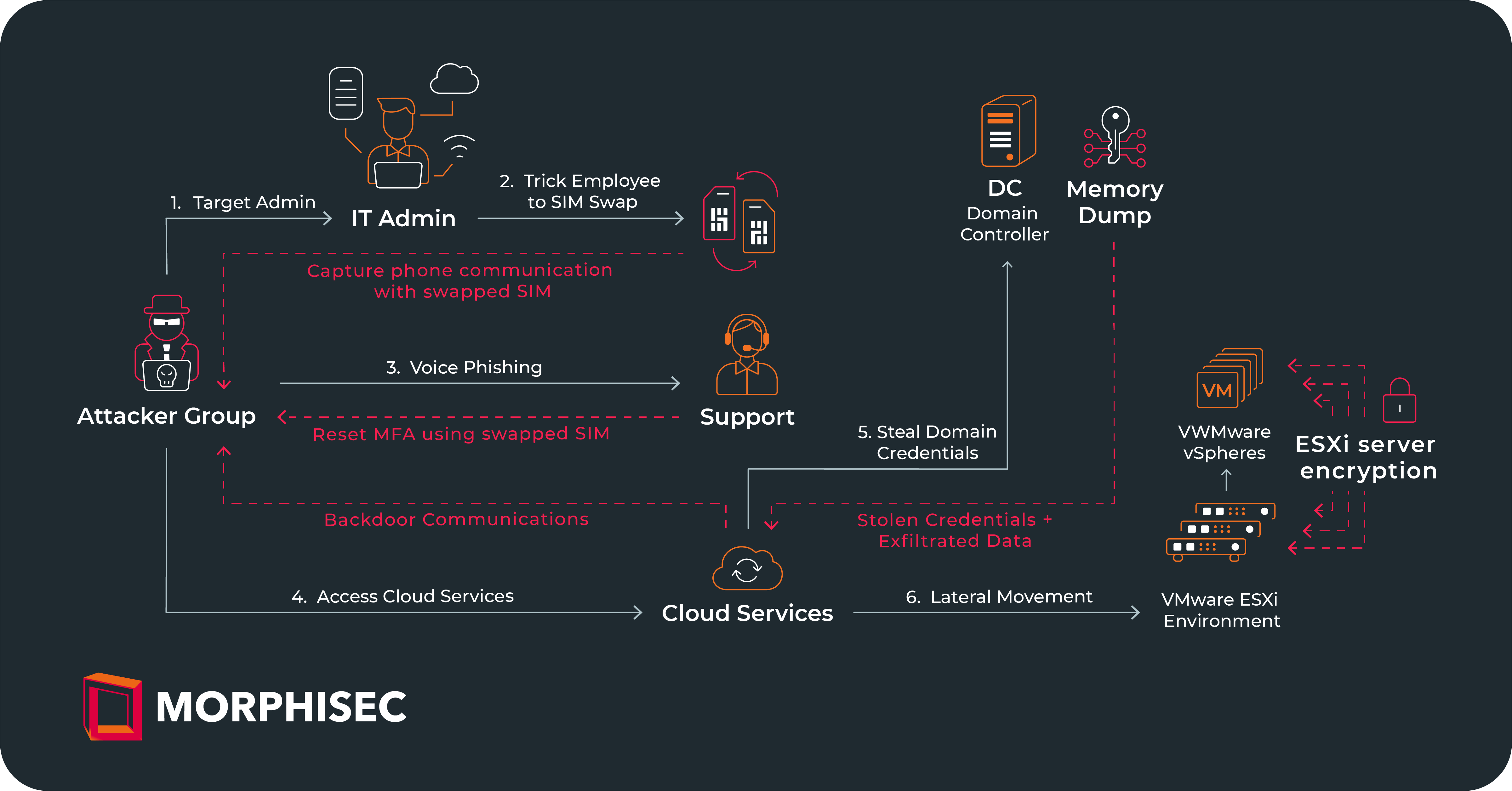
A full blown cybersecurity whodunit, with a plot even Hollywood would envy, unfolded during the attack. Playing the villain were ransomware groups ALPHV, Blackcat, and Scattered Spider; they intrusively claimed responsibility. Apparently, they sneaked around MGM’s network, implanted backdoors, and gained super admin privileges. They even hinted at having made copies of significant data. And guess what? They warned of the possibility of releasing sensitive, personal identifiable data, if things didn’t work out for them.
I came across a possible sequence of the attack flow: The cybercriminals supposedly targeted an MGM administrator, performed SIM swapping, fooled the IT Helpdesk into sending them a MFA reset code, and gradually gained control of the entire network. Talk about a technological horror movie in the making!
But when you think about it, weren’t we given cues all along? These groups specialize in targeting admin employees and getting crucial access. Seems like they put their access to good use—their posts indicated that they had access even after MGM took drastic countermeasures.
It seems the group also managed to get away with vital data. They hinted at notifying Troy Hunt from “HaveIBeenPwned” if they couldn’t strike an ‘agreement’ with MGM. Chilling, isn’t it?
They then encrypted around 100 ESXi servers once MGM tried to isolate critical assets post-breach. You can imagine the havoc it caused afterwards.
What can we learn here? First of all, the importance of contingency planning. Conducting simulation exercises, improving and verifying backup and restoration procedures, and a disciplined validation of these processes can be vital in incident recovery.
Next, we all need to bolster our cybersecurity defenses. A robust strategy that includes a well-segmented network and ironclad cyber defenses can lend you a big hand in deterring cyberattacks.
Lastly, aligning incident response framework and practices with your company operations ensures that everyone knows what to do when heavens forbid, an attack happens. This leads to prepared, thoughtful, and effective responses.
This incident underscores the need for vigilance and preparedness in the face of sophisticated cyber threats. Secure our cyber universe… one byte at a time, my friends!
by Morgan Phisher | HEAL Security