Hey there, Bay Area folks! I’ve got some interesting insider info to share with you today about what’s going on in the automotive cybersecurity landscape. Let’s dive right in.
You know how our Bay Area tech scene has been buzzing about Software-Defined Vehicles or SDVs? As these tech-forward vehicles inch closer to reality, we’re seeing a rising wave of cybersecurity threats tagging along, aimed specifically at our future wheels.
Sidenote: Ever wondered why? Well, SDVs are stuffed with intricate software and are mostly connected cars, making them irresistible targets for hackers aiming to wreak havoc. Last year, we saw the United Nations bring in UN-R155, a regulation meant to embed security into the design and production of vehicles. These new security regulations are now adopted by folks across the globe.
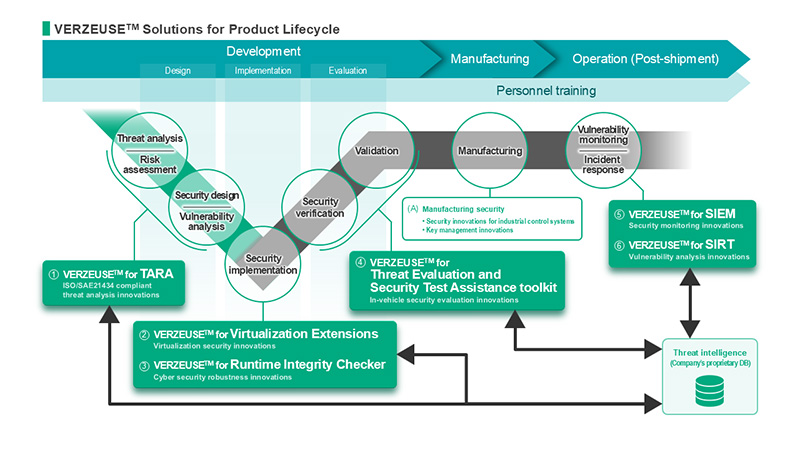
Beneath these layers of car-loving conversations lurks a point that many have not pondered: how do we manage cybersecurity across the entire vehicle lifecycle? From design and implementation to evaluation, production, and operation, there’s an enormous amount of effort needed for countermeasures against cyber vulnerabilities.
For those of you who are all, “Wait, what’s the vehicle lifecycle?”, here’s a quick rundown. We are referring to all the stages a vehicle goes through from its initial design, all the way to when it leaves the showroom floor. This includes the development and design phase, the implementation and production of parts, the evaluation of the finished product, and the operation of the vehicle after it’s been sold.
Now, picture a solution that streamlines this entire process while upholding high-quality security standards. That’s the whole idea behind the creation of innovations like the VERZEUSE™ series. This smart, containerized virtualization system is designed to combat cyber attacks at every lifecycle stage of the vehicle. It’s already winning applause from car manufacturers, who love its uniqueness and effectiveness.
The tool is pretty terrific, trust me. Through its Threat Analysis and Risk Assessment (TARA) system, it automates threat analysis during the design and development phase. Even if you aren’t a cybersecurity expert, it’s a handy tool to determine security requirements based on in-vehicle device characteristics.
But what really blows me away is the attack detection and protection solution called the VERZEUSE™ for Virtualization Extensions Type-3. It’s equipped to handle the security needs of next-gen cockpit systems. Here’s the coolest part: it has a real-time monitoring function, checking communications to block abnormal activity, and protecting the vehicle’s critical functions from potential attacks.
So, we’ve got user-friendly innovations which ensure security throughout the automobile’s lifecycle. Unbridled excitement about SDVs. And all the while, we are rising to the global challenge of making vehicles safer through bulletproof cybersecurity. The future of automotive technology, indeed, seems thrilling!
That’s enough for now. Keep an eye out for more insider updates on the unique crossover between the automotive, healthcare, and cybersecurity world. Catch you on the flip side!
by Morgan Phisher | HEAL Security