Network penetration testing is a cybersecurity practice where ethical hackers mimic cyberattacks on an organization’s network to identify vulnerabilities and enhance security defenses. The process involves pre-engagement activities like defining scope and obtaining authorization, reconnaissance such as network mapping, vulnerability analysis, exploitation, and post-exploitation actions like data access evaluation. Finally, vulnerabilities found are analyzed and reported, and changes are made to bolster network defenses. This checklist asserts the importance of regular network penetration tests in maintaining data integrity and system security.
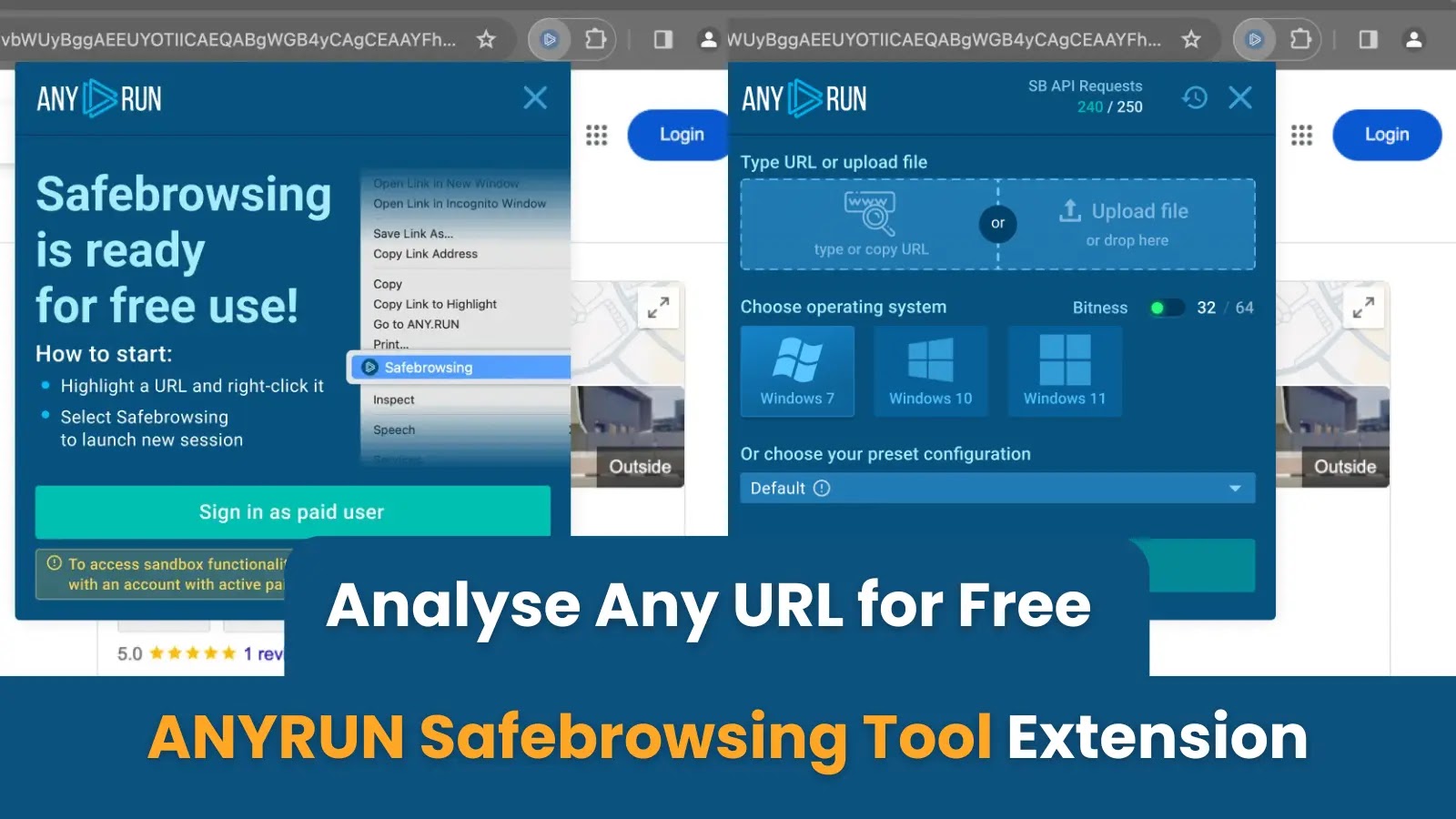
Use ANYRUN Safebrowsing Extension to Evaluate Any Suspicious URL for Free
Hey there, fellow Bay Area techie! Let’s dive into some cool cybersecurity updates that come straight from the world-class leader in Interactive Malware sandboxes –