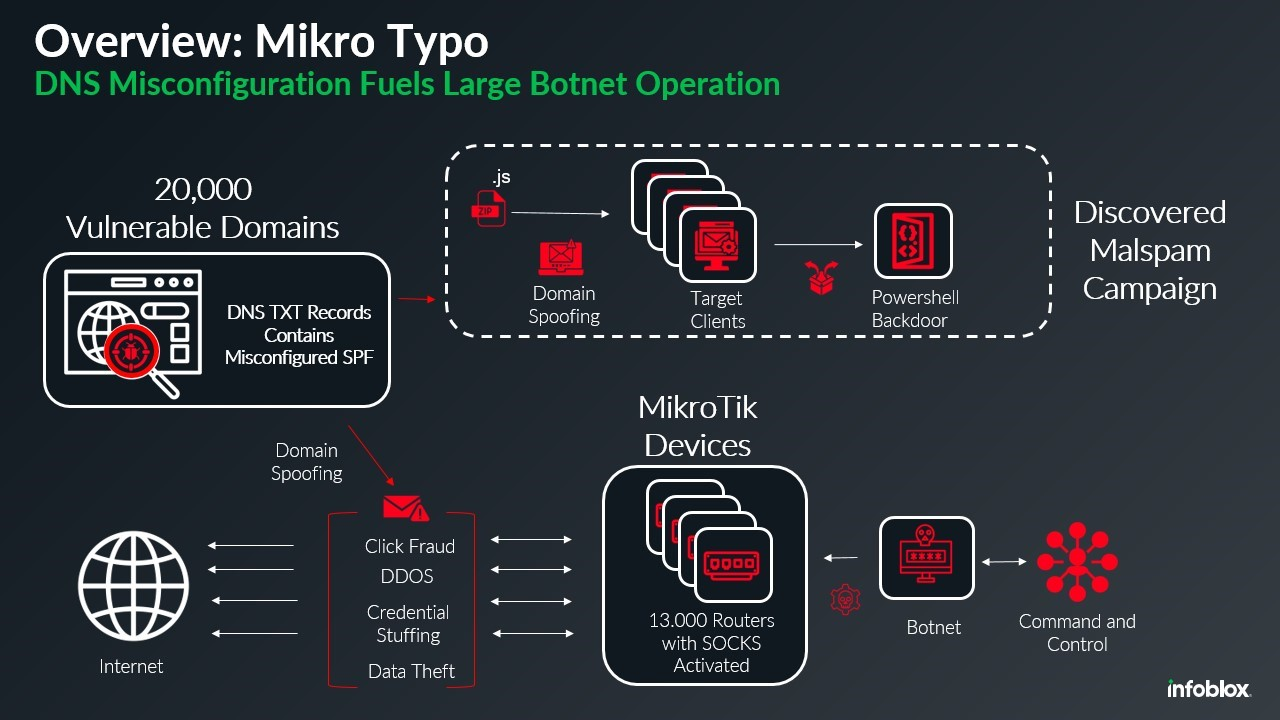
A 13,000-device MikroTik botnet is spreading malware by exploiting DNS misconfigurations. The malware is delivered via spoofing 20,000 domains and bypassing email protections; the botnet employs MikroTik routers to mask malicious traffic origins and boost the scale of its operations. Researchers have also discovered that botnet operators are exploiting improperly configured DNS records to enable any device to spoof legitimate domains in emails.

ASTP appoints 3 new health IT leaders: CTO, CDO and CAIO
The US Department of Health and Human Services (HHS) has filled three key technology roles. Alicia Rouault, formerly of the White House’s United States Digital