Hey, Bay Area folks! Today, we’re going to chat about OpenCTI and ANY.RUN, and an exciting interface between the two. OpenCTI is a nifty platform that collects and organizes threat data from various sources, sort of like a hub for all that scary cybersecurity stuff out there. ANY.RUN, on the other hand, is a stellar cloud-based service crawler that methodically scans suspicious files in a safe virtual environment.
Ready to get technical? OpenCTI uses ‘connectors’ (think digital importers) to bring in threat data from these various sources, which they then store as ‘observations.’ This trove of information includes things like IPs and hashes – basically, digital fingerprints of potential threats.
Now, where it gets exciting is that ANY.RUN has an ‘enrichment connector’ for OpenCTI, which means it streamlines threat analysis by probing the suspicious files and feeding the findings right back into OpenCTI. This creates juicy, context-rich indicators that can be super helpful for further investigation.
What’s more, with this enriched intel ready at your fingertips, it blends perfectly with your SIEM or SOAR systems. This initiates automated incident response procedures, putting your security team into turbo-mode at addressing potential threats.
When using OpenCTI, users can use the ANY.RUN connector to analyze these observations. With a straightforward click, it sets off an automated analysis (Isn’t technology just the best?). Once that’s done, it enriches the observation details with findings such as correlations between the observable and certain Tactics, Techniques, and Procedures (TTPs) identified as potentially indicating malware. Plus – it includes a link that will take you straight to the specific ANY.RUN sandbox analysis report for further digging.
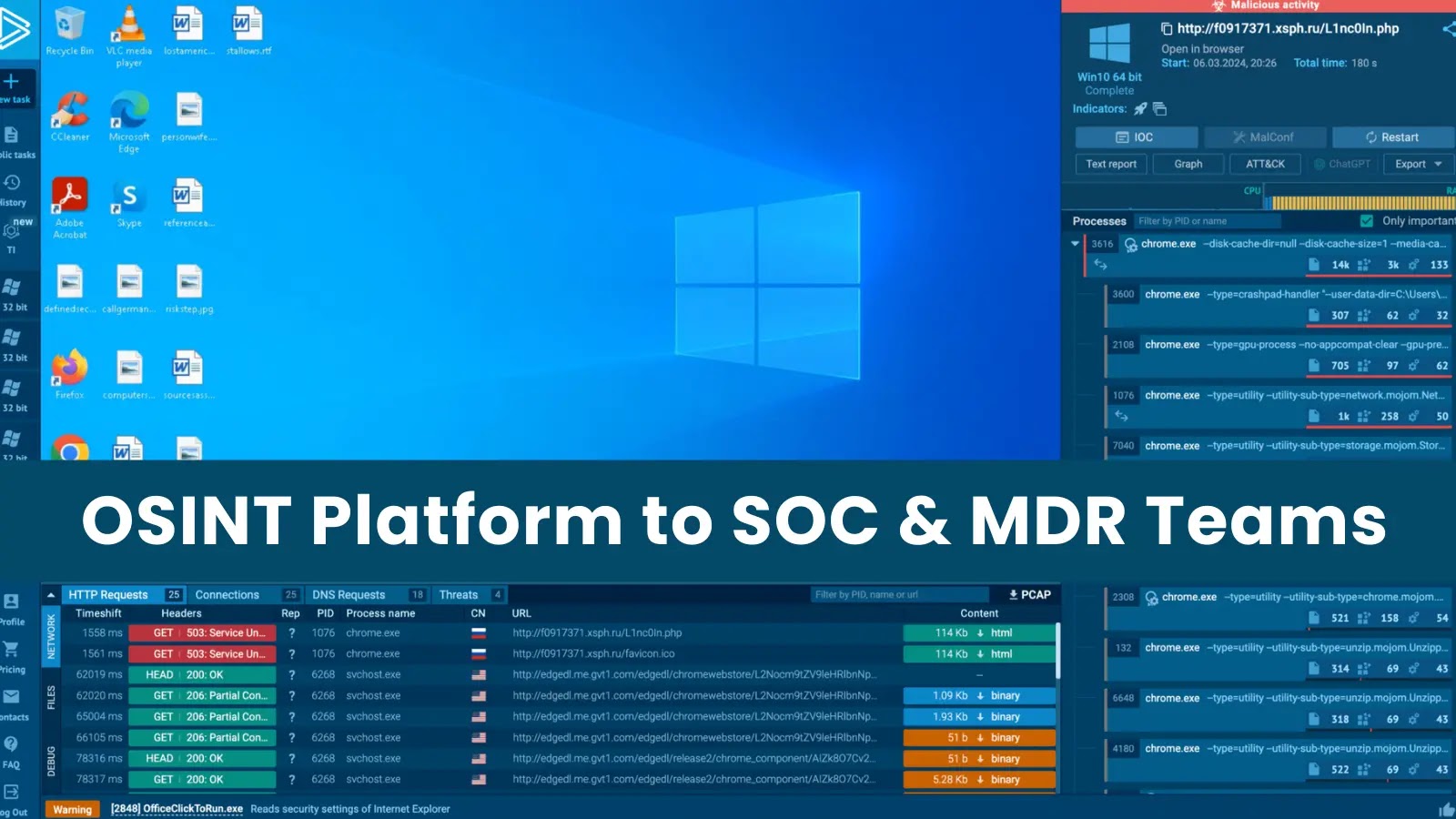
So, what’s the scoop on ANY.RUN? It’s basically a digital sleuth, a diligent cloud-based cybersecurity lab that really lightens the load for security teams. A whopping 400,000 professionals turn to ANY.RUN every day, using it to investigate events and boost their threat research speed for Linux and Windows cloud VMs.
ANY.RUN is a rockstar in its own right. Not only can it sniff out malware in real-time and identify many malware families within about 40 seconds of getting a file, but it also has an interactive feature that lets you live-connect with the virtual machine from your browser. As for the budgeters out there – don’t sweat it – ANY.RUN is a cost-effective option since it eases the workload on your DevOps team.
Plus, it’s a dream for onboarding new team members. ANY.RUN’s simple, user-friendly interface is a great space for even fresh-from-the-academy researchers to learn how to sift through malware and identify signs of compromise (You know, those pesky IOCs). So, that’s it! A quick dive into ANY.RUN and OpenCTI and their cool interface – Isn’t cybersecurity exciting?
by Morgan Phisher | HEAL Security