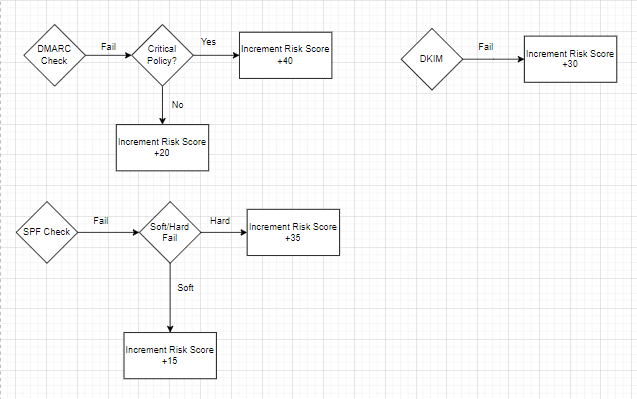
This article discusses building a phishing playbook using Smart SOAR, highlighting the importance of wireframing workflows. The four stages of the playbook include triaging, enrichment, containment and recovery. The article further breaks down these stages and describes how different responses and methods of assessment contribute to risk scores and severity level determination. Finally, it emphasizes the importance of integrating collaboration and approval processes within the workflow, aiding decision-making and validation.

Spain Arrests Alleged Leader of GXC Team Cybercrime Network – Infosecurity Magazine
Spain Arrests Alleged Leader of GXC Team Cybercrime Network Infosecurity Magazine


.png?w=0&resize=0,0&ssl=1)