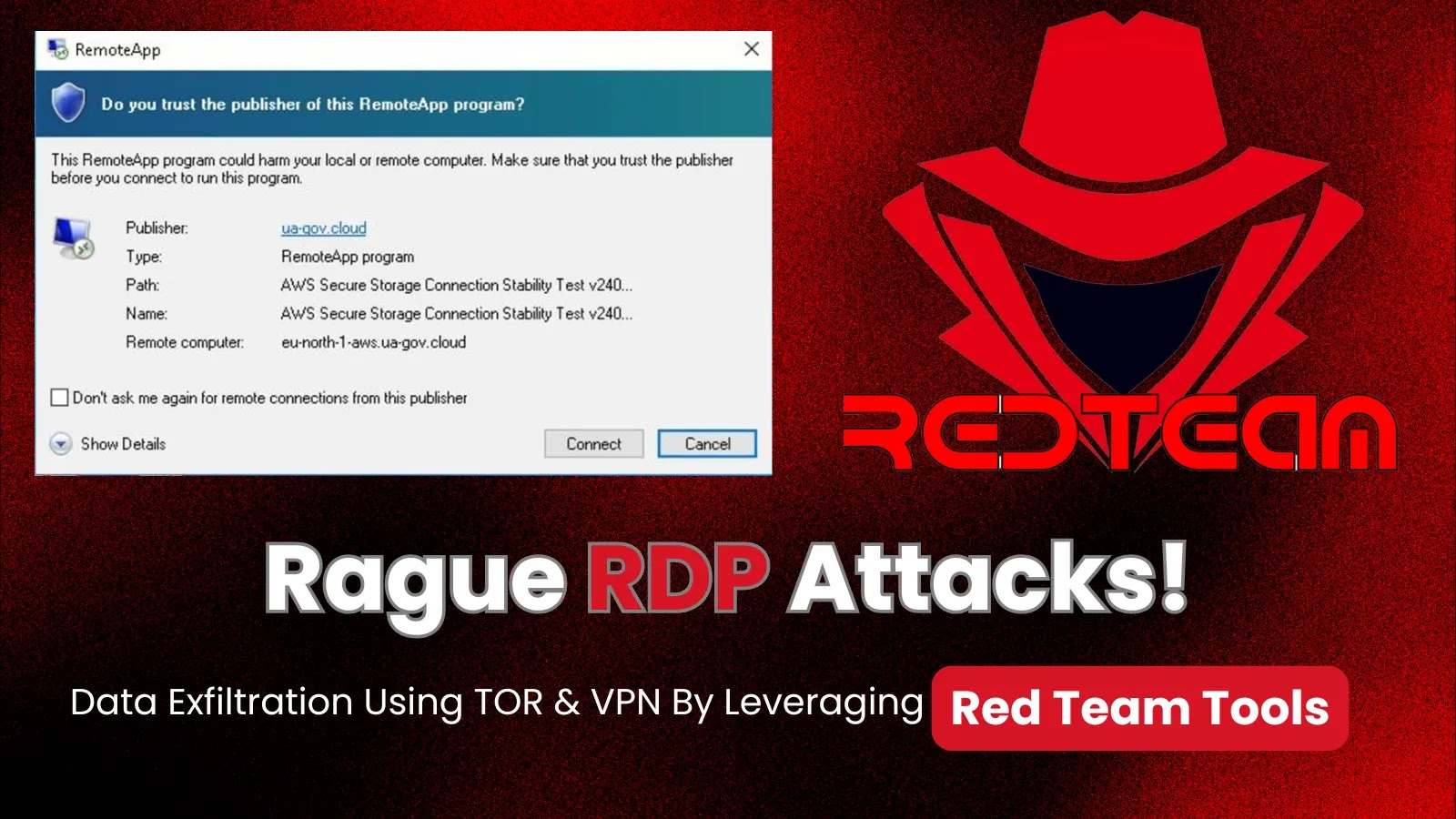
The advanced persistent threat (APT) group Earth Koshchei, also known as APT29 or Midnight Blizzard, has launched a major cyberespionage campaign. Using a method called “rogue RDP,” the group sent spear-phishing emails containing a malicious Remote Desktop Protocol file which, when opened, tried to connect to rogue servers. Various entities including governments, military organizations, and researchers were targeted, primarily for espionage purposes. Experts say the campaign demonstrates how genuine cybersecurity tools can be used maliciously, highlighting the need for stronger defensive measures.

The NCSC wants developers to get serious on software security
The NCSC’s new Software Security Code of Practice has been praised by cyber professionals as a significant advancement in enhancing software supply chain security.