Cyber attackers are using increasingly sophisticated techniques to evade detection, using methods such as simulating human behaviors to impersonate devices and exploit legitimate sessions, camouflaging their activity amid legitimate transactions, mimicking trusted brands to exploit user trust, altering or randomizing page elements to evade tracking, and using complex anti-research tactics to thwart analysis. Despite these advances, defenders can employ measures like phishing training, credential monitoring, threat detection, and regular configuration reviews to secure their defenses.
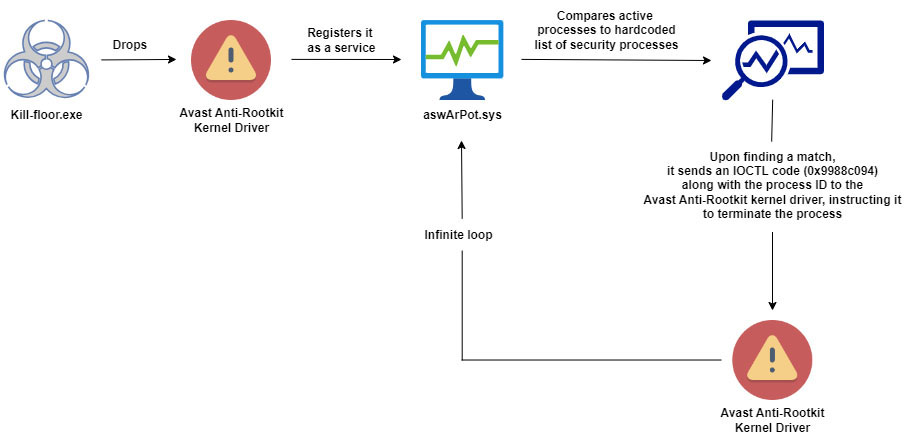
Malware campaign abused flawed Avast Anti-Rootkit driver
Threat actors are exploiting a flawed Avast Anti-Rootkit driver to bypass detection, disable security tools and compromise targeted systems, Trellix researchers found. The malware corrupts



