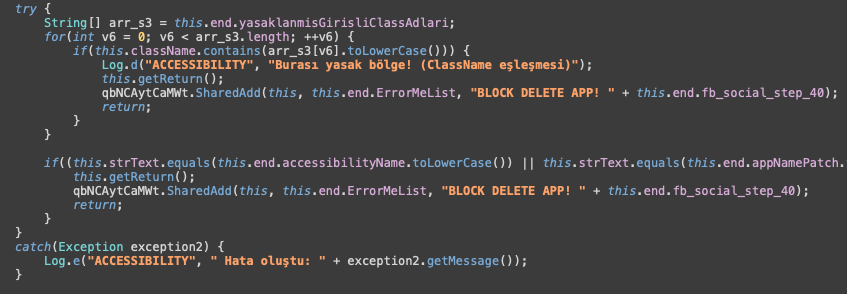
The new Android trojan Crocodilus exploits accessibility features to steal banking and crypto credentials. It mimics modern banking malware, uses overlay attacks, keylogging, and remote access, and connects to a malicious server, monitoring app launches, and using overlays to steal credentials. This software primarily targets users in Spain and Turkey.

What are business logic vulnerabilities?
Business logic vulnerabilities in software allow attackers to exploit flaws in design, enabling them to circumvent security measures and manipulate pricing, authentication, and other key