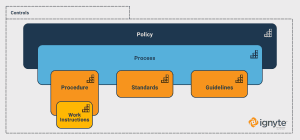
Cybersecurity is a complex field with many specialised terms. Four key terms are Policies, Procedures, Standards, Guidelines, and Controls. Policies are broad, high-level management decisions, standards define how to achieve those policies, controls are specific cases and directives to implement a standard, while procedures are the specific steps needed to implement a control. NIST and ISO are two agencies that define cybersecurity standards. These terminologies form the foundational architecture of a company’s cybersecurity protocol.

Linux USB Audio Driver Vulnerability Actively Exploited in the Wild Via Malicious USB
A critical vulnerability in the Linux kernel’s USB-audio driver, allowing out-of-bounds memory reads, has been patched by Takashi Iwai from SUSE. This flaw could let