Kiwi Radware user Feenix Communications becomes Radware reseller

Security tech firm Radware has signed a managed security service provider (MSSP) reseller agreement with Feenix Communications. The New Zealand-based firm will resell Radware’s application and network security solutions, which include Cloud DDoS protection and DefensePro DDoS protection. The telecoms firm has used Radware’s security technology for seven years.
Amazon Healthcare Program: Amazon Prime & One Medical, Explained

Amazon Prime has launched a primary health insurance scheme, leveraging its acquisition of One Medical. The low-cost plan, $14 a month, includes prescription coverage. However, questions have been raised about trade-offs in care quality, information security, and the increasing role of AI in healthcare decisions. Concerns also exist over Amazon’s track record of selling unsubstantiated […]
Global cyberattacks facilitated by Indian hack-for-hire company

Indian hack-for-hire firm, Appin Software Security, has been facilitating cyberattacks globally since 2009, targeting government officials and corporations, according to a report by SentinelOne. The company utilizes third-party contractors and various methods like data theft, malware, phishing, and intrusion tools for these operations. The firm also used the freelancing platform Upwork to facilitate malware acquisition.
Gamaredon’s LittleDrifter USB malware spreads beyond Ukraine

Researchers have discovered a worm called LittleDrifter, which is spreading via USB drives. Believed to be from a Russian state-sponsored group known as Gamaredon, it has infected systems in multiple countries, leading to suggestions of loss of control. The worm is written in VBS and designed to spread over USB drives, establishing communication with the […]
Malware Uses Trigonometry to Track Mouse Strokes
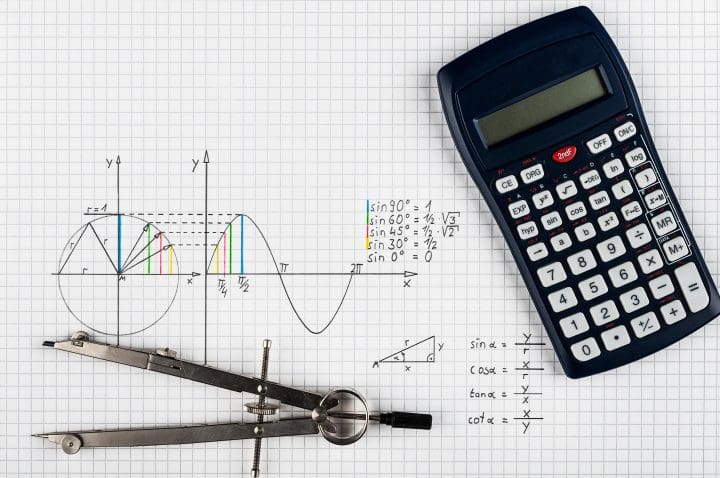
The latest edition of the LummaC2 malware-as-a-service utilises a new anti-sandbox feature, which uses trigonometry to track mouse movements and detect active human users on compromised devices. This function allows it to avoid revealing its secrets to the isolated sandbox environment used in cybersecurity defence. Although the use of trigonometry is seen as interesting, experts […]
West Virginia medical center goes live with Oracle Health

Greenbrier Valley Medical Center (GVMC) in Fairlea, West Virginia, has implemented the Oracle Cerner electronic health records (EHR) system. Along with the main hospital, three GVMC sleep clinics, two sleep labs, and seven specialty clinics in 13 locations have also adopted the EHR system between June and November.
CISA Publishes Supplement to HPH Cyber Risk Summary

The Cybersecurity and Infrastructure Security Agency has released a guide discussing vulnerabilities and best practice in IT health security. It highlights common cyber threats faced by the Healthcare and Public Health (HPH) sector, including web application vulnerabilities, encryption weaknesses and unsupported software, often leading to data breaches and ransomware. The guide offers solutions based on […]
NY State Eyes New Cyber Regs for Hospitals; $500M Price Tag
New York State is planning new cybersecurity regulations for hospitals, which include a two-hour window for reporting major breaches and the appointment of a Chief Information Security Officer. The proposed rules come with a request for $500m in funding to aid providers in boosting their cybersecurity in accordance with the new regulations. Hospitals may also […]
How State and Local Agencies Can Modernize Their Data Centers

Protecting citizen data is a key role for CIOs, requiring a holistic approach, safeguarding data and ensuring immutable backup systems. Agencies can streamline operations with automation tools, enhancing performance and security while reducing human error. A software-based approach can save millions annually. The public sector’s transition to the cloud has been slow, but it’s important […]
Digital Avengers: Five Unifying Factors Shaping the Battle Against Global Cybercrime
As cyber threats develop, a collective approach is crucial. This includes sharing information and threat intelligence, capitalizing on technological advances like AI, building secure systems by default, having standardised security approaches across all teams, and encouraging continuous cybersecurity education. Microsoft urges that the wider cyber community must work together in these areas to build global […]