a driving force in biotech advancements
Qatar Investment Authority (QIA), the country’s sovereign wealth fund, has been a significant player in the biotech industry since 2020. Using oil and gas resources and a diversification strategy, QIA has grown to become one of the ten largest Sovereign Wealth Funds globally. Investing in biotech to fulfil Qatar National Vision 2030, QIA has supported […]
Patient details at Tayview practice in Fife leaked in data breach

Patient details from Tayview practice in Fife were leaked due to a data breach.
Sekur Private Data Ltd. Launches SekurRelay Enterprise Email Solution for C-Level Executives and High-Level Employees, Eliminating Roadblock to Mass Adoption of Sekur by Enterprises and Governments

Sekur Private Data has launched SekurRelay, an enterprise email solution. The software allows staff to migrate business email onto the Sekur platform, enjoying its privacy and security features, but retaining the same business email domain as their colleagues. This service, geared towards senior employees and government officials, guards against Business Email Compromise attacks. It offers […]
Sekur Private Data Ltd. Launches SekurRelay Enterprise Email Solution for C-Level Executives and High-Level Employees, Eliminating Roadblock to Mass Adoption of Sekur by Enterprises and Governments

Swiss secure communications platform Sekur has launched its SekurRelay Enterprise Email Solution, enabling executives and management to split their company email domain in two. Company employees can seamlessly migrate existing business emails to Sekur’s secure platform while keeping the original domain. The offering protects against Business Email Compromise (BEC) attacks and is aimed at encouraging […]
Spin.AI Brings Powerful All-in-One SaaS Security Platform to Google Cloud Marketplace

SaaS security firm Spin.AI has launched its all-in-one security platform, SpinOne, on Google Cloud Marketplace. The system protects SaaS data from threats such as misconfiguration, ransomware and data leaks. It offers enhanced security, compliance and SecOps efficiency while being designed to protect data in applications like Google Workspace, Microsoft 365, Salesforce and Slack.
8 things every physician must know to stop cyberattacks

In 2021, over 700 health data breaches, affecting 45 million patient records, were reported to the U.S. Department of Health and Human Services. Approximately 75% of these incidents were linked to cybercriminals, who find medical data ripe for exploitation in fraud schemes. An eight-part video series by the American Medical Association (AMA) explains how such […]
Ddostf DDoS Malware Attacking MySQL Servers in Windows

Vulnerable MySQL servers are being attacked by Ddostf DDoS bot which is capable of launching Distributed Denial of Service attacks. Ddostf, first identified in around 2016 and believed to have been built in China, supports both Windows and Linux platforms. The bot malware is considered unique due to its ability to sell subsequent DDoS attacks […]
Pay more attention to customer data privacy

The text encourages individuals to be more attentive to their data privacy. While cookies are stored on users’ computers to enhance their experience and serve personalized content, the authors maintain that they do not track users’ information on their site. They use a minimum of one cookie to remember users’ privacy preferences.
Yes, people are still using ‘password’ for their password

Despite ongoing warnings about password security, “password”, “123456” and “123456789” remain popular choices, according to a report by password-management firm NordPass. Over 70% of the passwords could be cracked in less than a second. NordPass also found that 31% of the passwords comprised numerical sequences, or contained names, common words, and phrases. Interestingly, users have […]
Cyber Security Glossary: Terms Every Small Business Manager Must Know
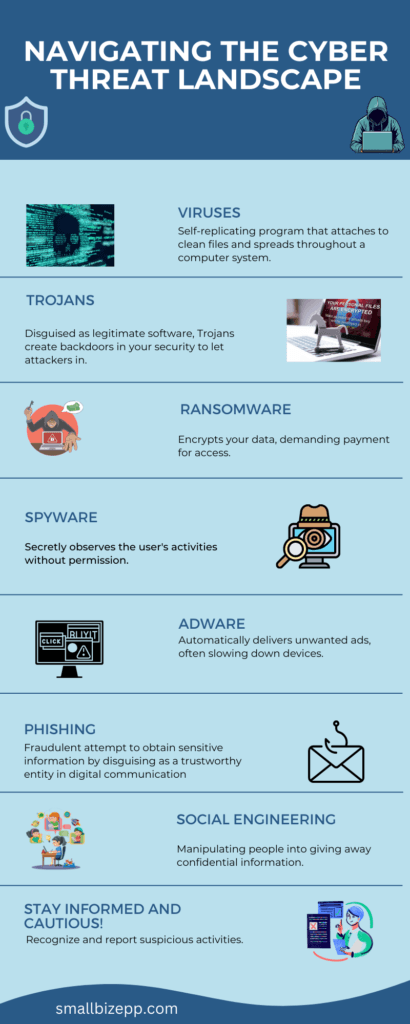
The article provides a comprehensive guide to key cybersecurity terms for small business owners, underscoring the importance of understanding these to effectively communicate with IT personnel and make informed decisions concerning business asset protection. It covers cyber threats such as malware and phishing, defense tools like firewalls and antivirus software, data protection strategies, incident response […]