Palestine-aligned cyberespionage actor shifts infection chain tactics

Cyberespionage group TA402, known for targeting government entities in the Middle East and North Africa, has altered its infection chain tactics three times recently, despite no observed change in its targeting. Its recent campaigns use spear-phishing emails sent from compromised email accounts of legitimate entities, delivering custom malware implant, IronWind. The group’s activities overlap with […]
At Last, A Healthcare ‘Pod’ Experience At The Gym

Healthcare technology company Forward has launched CarePods; AI-driven, walk-in healthcare units that offer services like cancer screening, blood work, and mental health assessments. Available for a $99 monthly fee, the pods will start appearing in cities like San Francisco, New York, and Philadelphia. However, a Pew Research poll indicates 60% of Americans are uncomfortable with […]
North Mississippi Health Services Affected by MOVEit-Related Data Breach at Cadence Bank | Console and Associates, P.C.

North Mississippi Health Services (NMHS) has announced a data breach at Cadence Bank, impacting consumers’ sensitive information. The breach was caused by an unauthorized party exploiting a vulnerability in the MOVEit file transfer application. Those affected had their names, addresses, dates of birth, social security numbers, driver’s license numbers, and medical and financial information exposed. […]
LENZ to Merge with Gene Editing Therapy Developer

Graphite Bio is set to merge with LENZ Therapeutics through a reverse merger, via an all-stock transaction. The merged company will continue to operate under the name LENZ Therapeutics and trade on the Nasdaq under the ticker symbol “LENZ”. The merged entity will focus on advancing LENZ’s pipeline candidates intended to address presbyopia, with an […]
Israel Hit by Evolving BiBi Malware Surge

Clorox’s Chief Information Security Officer, Amy Bogac, has stepped down following a major cyberattack in August. This week, Israel also faced a surge in cyberattacks from BiBi malware. Meanwhile, the US FCC has proposed a Cybersecurity Program for Schools. The UK ICO warned shoppers about smart device security ahead of Black Friday. A pro-Palestine APT […]
MySQL servers targeted by ‘Ddostf’ DDoS-as-a-Service botnet

AhnLab Security Emergency Response Center (ASEC) researchers have discovered a DDoS-as-a-Service campaign by the ‘Ddostf’ malware botnet, which targets MySQL servers. The botnet enslaves breached servers by exploiting vulnerabilities in unpatched MySQL environments or brute-forcing weak administrator account credentials. To defend against the attack, the researchers recommend applying the latest updates and creating long, unique […]
Advisory from CISA: Warnings about Scattered Spider
Hello chaps! Gather round, I’ve got a tale straight from the digital exchange of today: a captivating yarn about digital highwaymen, some sort of Scattered Spider they call themselves, who are brazenly shaking down corporations left and right, going after their technology support lines. Our mates at the Federal Bureau of Investigation (FBI) and Cybersecurity […]
Using AMTD to Prevent Unidentified and Indiscernible Attacks That NGAV, EPP, and Endpoint Detection and Response Solutions Overlook
Hello Bay Area community, we gotta chat about cybersecurity. It’s like this relentless game of cat and mouse out there, and we’re struggling to keep up. Have you noticed that? We’re dealing with hacker jargon like fileless, in-memory, zero-days exploits, and my goodness, they sure have some evasive techniques in their bag of tricks. These […]
AI roundup: HEALWELL AI buys LLMs, Forward to roll out staffless health kiosks
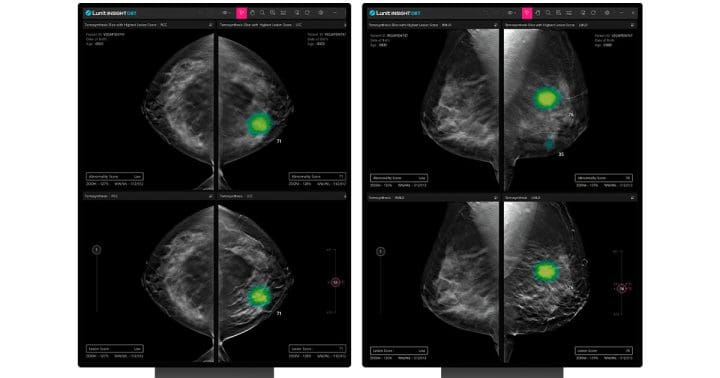
HEALWELL AI is set to acquire Pentavere, broadening its AI-based decision support for early disease diagnosis. Meanwhile, Google AI veteran’s Forward Health will launch doctor-built CarePods in major cities. These AI-driven diagnostic rooms provide disease detection, biometric scans, and blood tests among other services. Additionally, AI-powered cancer diagnostics provider, Lunit, has obtained FDA approval for […]
Building a Robust Incident Response Plan
A robust incident response plan against data breaches should include identification, protection, detection, response and recovery. Companies need to understand their roles in response to breaches and the legal implications. Prevention strategies include regular risk assessments and staff training, sophisticated security platforms, and regularly updating security measures. Effective communication during a breach, swift containment and […]