Remote Work Security Market Worth $136.0 billion by 2028,

The global Remote Work Security Market is set to expand from $51.7bn in 2023 to $136bn in 2028, with the increased need for data privacy at a legislative level driving the change. Regulatory imperatives like the EU’s GDPR and the US’s CCPA are forcing organizations to adopt secure remote work systems. Key players in the […]
substantial Q3 leads Europe’s recovery

The UK biotech sector saw an impressive surge in funding in Q3 2023, recording a 48% increase from the previous quarter, marking a record-breaking period for the sector. Despite global economic uncertainties, the sector showed steadfast growth, with venture capital playing a pivotal role. Significant deals included Oxford University spin-out Beacon Therapeutics securing £96.6m ($120m) […]
An introduction to IoT penetration testing
Complex IoT systems could have security vulnerabilities that are hard to spot in time. IoT penetration testing or pen testing simulating a cyber attack can reveal these weaknesses before a real attack. Common challenges include weak passwords, insecure network services, outdated components, and insecure data storage and transfer. Pen testing involves planning, scanning the system, […]
SBOM formats compared: CycloneDX vs. SPDX vs. SWID Tags

Software bills of materials (SBOMs) inventory applications and are an important measure for securing an organization’s software supply chain. Three common SBOM formats are CycloneDX, which is particularly useful for tracking vulnerabilities; Software Package Data Exchange (SPDX), which is often chosen by larger organizations due to its license management ability; and Software Identification (SWID) Tags, […]
Malware Spotlight – Into the Trash: Analyzing LitterDrifter

Russian espionage group, Gamaredon, has been using a new self-propagating worm dubbed LitterDrifter to target nearly exclusively Ukrainian entities. The worm is spread via USB drives and maintains communication with a set of command-and-control servers. Its design supports large-scale data collection while remaining simple, effective, and focused on regional targets. Although the primary targets are […]
Malicious Google Ads Trick WinSCP Users into Installing Malware
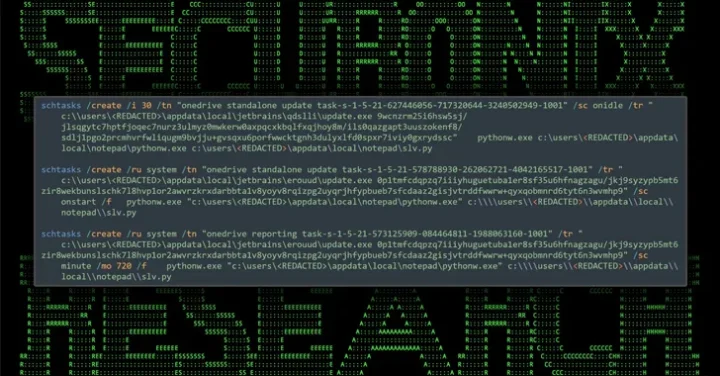
Threat actors are using manipulated Google search results and malicious ads to trick users into downloading malware disguised as legitimate software such as WinSCP. The cybercriminals leverage Google’s Dynamic Search Ads to serve the malware-infected ads, which direct users to a phishing site where they download the malware. Cybersecurity company Securonix, which is tracking the […]
Roshan Navagamuwa hired as EVP and Chief Information Officer at AIG

Roshan Navagamuwa has joined AIG as EVP and CIO.
Metadata in Blockchain Transactions Explained
Metadata, which includes timestamps, transaction details, smart contract data, and more, enables various functions and storage capabilities in blockchain networks. Metadata in blockchain is used in sectors such as healthcare, digital identity, smart contracts, and nonfungible tokens (NFTs). However, challenges including scalability issues, data security concerns, and Oracle dependability must be addressed for broader implementation. […]
Fastly report highlights cybersecurity challenges in media sector

Fastly’s cybersecurity report highlights that cyber attacks have cost media businesses an average of 9% of their annual revenue this year, with the industry being particularly vulnerable. In response, 71% of media companies plan on increasing cybersecurity budgets. It also reveals a talent shortage in cybersecurity, with a third of professionals attributing recent security issues […]
Businesses that eliminate passwords report better security outcomes

New research indicates that organizations utilizing passwordless technologies have fewer instances of phishing attacks, increased productivity, and higher employee satisfaction compared to those using traditional password-based systems.