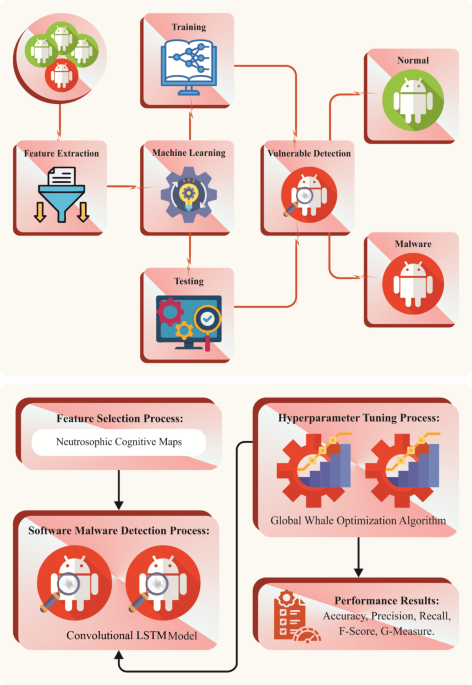
Summarize this content to a maximum of 60 words: The Omnibus Rule has clarified that a person or organization can be classified as a business associate based on the activities performed on behalf of covered entities or other business associates regardless of whether there is a formal business associate agreement in place.With this classification, they also now become liable for any impermissible uses and disclosures of protected health information and are subject to the HIPAA civil and criminal penalties to business associates and subcontractors. The Omnibus Rule also classifies a person or organization that maintains or transmits PHI as business associate even if they do not access or view the information. All of these recent changes present a clear sign to small businesses that they need to address the risk and compliance necessary.Many organizations calculate their risk by looking at the breach notifications requirements as outlined by the 2009 HITECH Act. The chain of reporting for a business associate is to notify the covered entity without reasonable delay and no later than 60 days from the discovery of the breach. If the breach affects fewer than 500 individuals the covered entity has to report to the Secretary of the Office of Civil Rights on an annual basis no later than 60 days after the end of the calendar year in which the breach occurred.As a result, it may take up to a year to have a breach reported to the OCR.Further it’s unlikely that any breach affecting fewer than 500 individuals would make the public “wall of shame.” This is not a great way to measure risk. Earlier this year the OCR announced its first HIPAA breach settlement involving less than 500 individuals. In the end, the organization was ordered to pay a $50,000 fine for just one stolen laptop.Going forward covered entities are being advised to implement formal BA agreements, even for contractors that address applicable privacy and security rule provisions. There is a strong likelihood that many agreements may dictate specific security standards. For business associates that support multiple entities, this may be problematic. When the final HIPAA security rule was published, the security standards were designed to be ‘technology neutral’ to accommodate change. This agility opened up many questions on which technologies to deploy and how to achieve HIPAA compliance.Business associates may add the physical, administrative, and technical safeguards that are required and leverage this as a business differentiator. NIST Special Publication 800-66: An Introductory Resource Guide for Implementing the HIPAA Security Rule is a great place for business associates and organizations to start increasing their knowledge of the procedures and controls. Risk assessments can also help identify the gaps in the outlined safeguards.Protection from malicious software as an addressable specification is classified in the security standards matrix as being part of administrative safeguards for security awareness and training. In some guidelines this risk can be mitigated with a procedure that educates the users about guarding against, detecting and reporting malicious software and training employees to know the importance of timely application system patches.In 1996 when HIPAA security standards were conceived this was an appropriate action to mitigate risk. Today, with more than 100,000 new malware threats being discovered a day, reasonable security can only come from centralized endpoint protection for the systems supporting the business and should include device control and encryption.Encryption criticalMany of the incidents as reported to HHS were breaches that occurred from the direct result of stolen or lost laptops and USB media. Encryption is clearly called out as a technical safeguard for protecting the PHI transmissions. As more mobility is enabling business, this should be applied to any system or device that may be easily used outside of the physical safeguards for the systems of the business, even for systems that are never intended to leave the premise.Continued education and awareness training is also recommended to ensure that the organization knows that the sharing of passwords and passphrases – or worse, having these taped to the systems themselves – will damage the organization. Encryption does not guarantee safe harbor.Providing protection for PHI in a digital world will continue to require deeper education, more efficient solutions and ongoing awareness. Healthcare has been relatively lucky in that the majority of the types of breaches as reported through HHS have not involved large scale cyber-attacks like those now being experienced through denial of serve attacks in the banking sector.Healthcare, with a wider adoption of encryption and advanced malware protection, can help minimize the very preventable unauthorized access to PHI. It will also help to thwart a very real threat of ransomware where cybercriminals enable their own encryption on your systems to block access while demanding a ransom to unlock the data. The Omnibus Rule with regards to extending the definition of business associates is a step in the right direction to expanding the safeguards needed in our digitally connected business environments.

100 MILLION Americans in UnitedHealth PII Breach
UnitedHealth confirmed that February’s ransomware attack impacted 100 million people, the largest healthcare data breach in the US. Health insurance, health, billing, and personal information