Using a UIA caching mechanism, cybercriminals can stealthily interact with elements not shown on screens, like reading and sending messages. This applies to other applications; for instance, they can detect credit card information being typed on an online shopping site or manipulate the address bar to redirect users to a malicious website without raising suspicion.
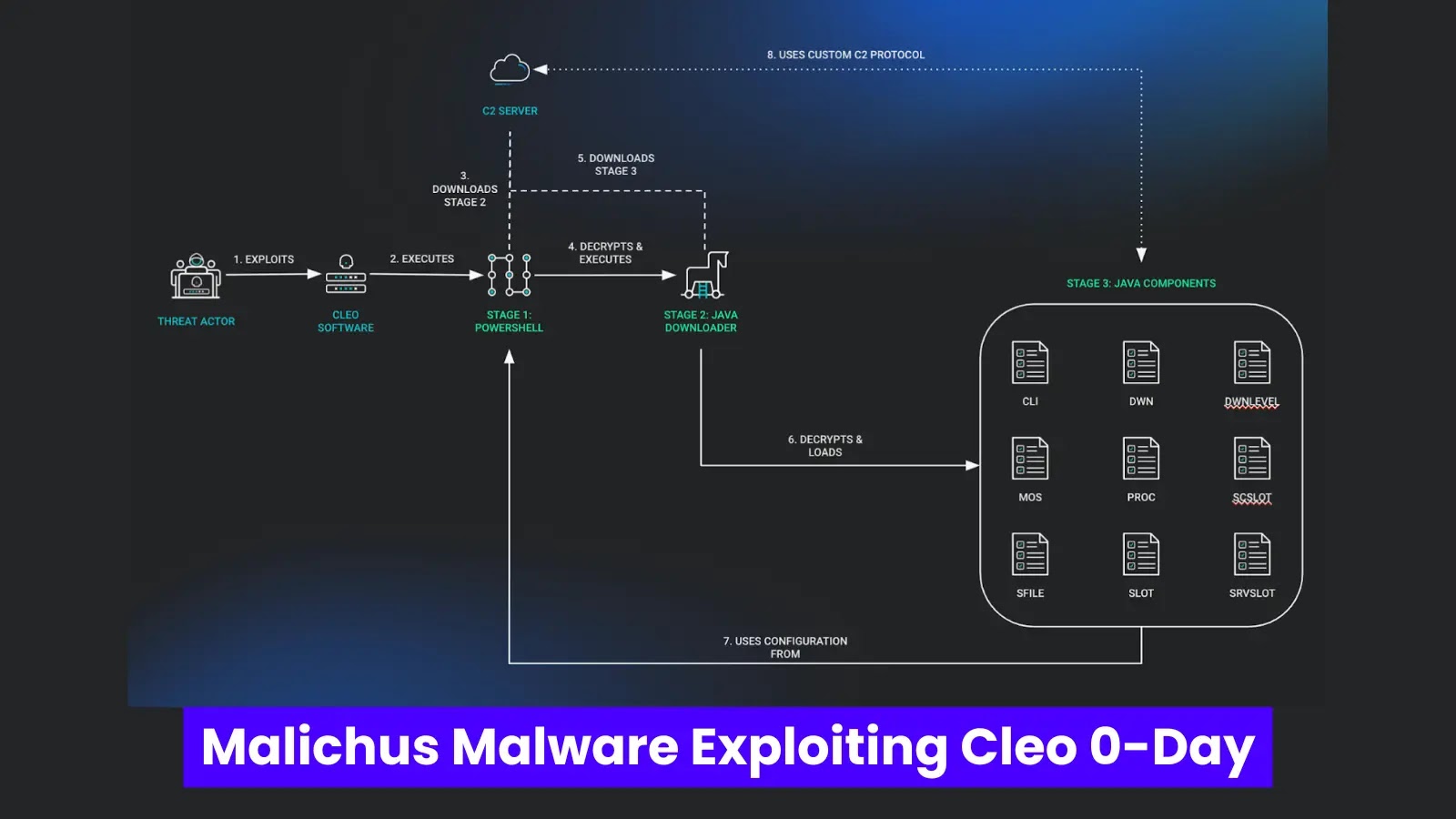
Malichus Malware Exploiting Cleo 0-Day Vulnerability In Wild
Hackers are actively exploiting a high-risk vulnerability in Cleo’s file transfer products, Harmony, VLTrader, and LexiCom, causing severe risk to businesses. A malware named Malichus