Reading about this fascinating tool that enhances cybersecurity for Android devices really caught my attention. These days, we all know how important it is to be aware, protect our data and guard against cyber threats, especially when it comes to our mobile devices. Let’s step into the world of cyber risk analysis, specifically for Android OS – I promise it’s not as technical nor as intimidating as it sounds!
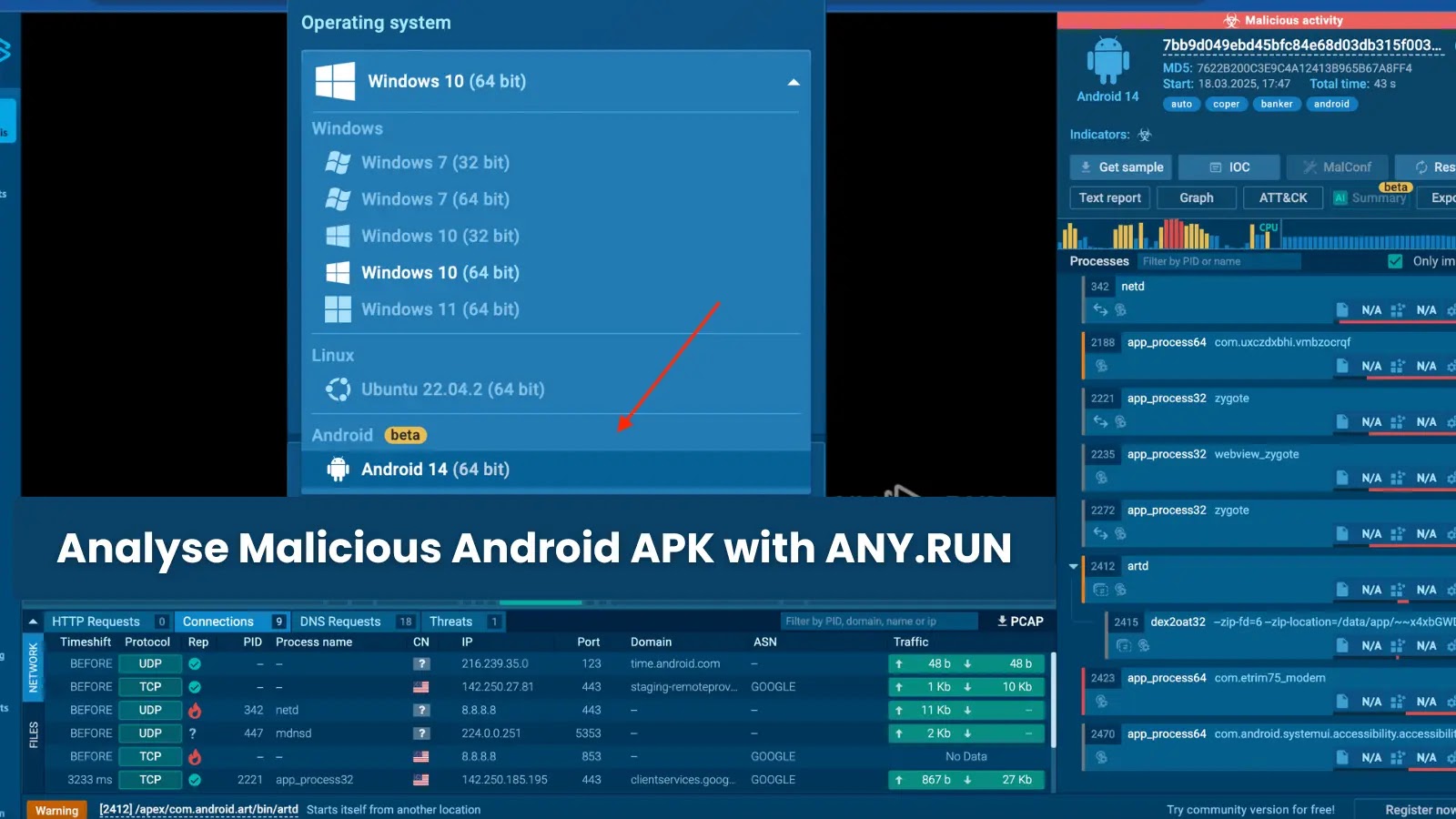
So, there’s this interactive malware analysis platform that has now extended full support to Android OS in its sandbox environment. With this new function, cyber security teams can delve into Android malware with incredible detail and efficiency. It’s almost like giving them an Android-specific magnifying glass to scrutinize any potential threats.
You see, this new feature works wonders to plug the gaps and eliminate makeshift analysis methods. It’s akin to putting malware under a microscope within a ‘sandbox’ that mimics how it would behave on a real mobile device. Android devices are increasingly targeted by attackers aiming to steal credentials, infiltrate corporate networks and tamper with financial systems.
Analysing suspicious files in real-time, this platform brings forth detailed insights about the malware’s behavior – whether it’s misusing permissions, purloining data, or establishing dodgy network connections. Security teams can analyze threats without hampering operations or adding more workload. Moreover, this analysis happens within the confines of this ‘sandbox’, ensuring there’s no third-party intrusion.
Now, you might be wondering how this works. Well, users can upload suspicious files directly into the sandbox after opting for Android OS. The fascinating part is, the platform runs the file and displays its behavior in real-time. It even accommodates adjustments like screen orientation to better replicate the usage on a mobile device.
The great advantage is that it allows security teams to engage with the apps as if they were operating on a real Android device. What this means is, they can launch malware-infected apps and watch their behavior, or grant or deny permissions to see how apps respond. It’s like putting the malware on a stage and shining a spotlight on it!
A feature named Process Tree was particularly eye-catching to me. It furnishes a structured overview of all executed processes, making it uncomplicated to detect connections to suspicious services or commands or uncover attempts to execute additional payloads. It’s an easy-to-understand, visual representation of how an app interacts with the system, eliminating the need for tedious log tracking.
Perhaps one of the best perks is that after completing an analysis, the system generates detailed reports containing actionable information. These reports identify malicious URLs or IP addresses, the files that were modified or dropped, distinct changes to the system, etc. These revelations are invaluable for updating security rules and obstructing future attacks.
Even small teams can avail of these mobile threat analysis capabilities without any additional expenses. It’s a tangible testament to the democratization of access to advanced cybersecurity tools, protecting Android devices from potential threats.
With more than half a million cybersecurity professionals already using this tool for Windows and Linux systems, its Android OS extension is genuinely a game-changer. We’re looking forward to how this platform will continue enabling faster detection, deeper insights, and more efficient mitigation of Android cyber threats.
by Morgan Phisher | HEAL Security