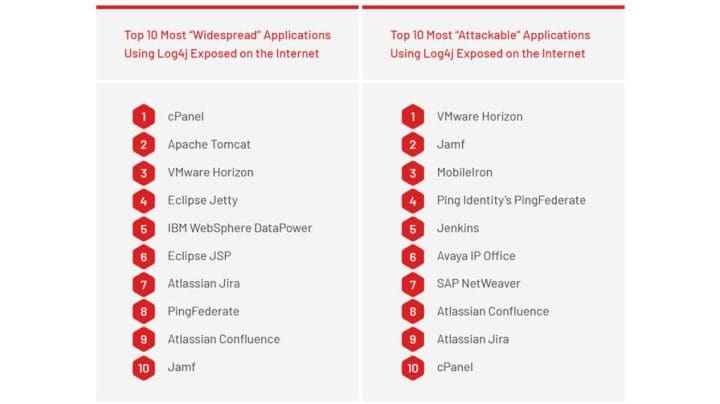
Not all software utilizing Log4j is equally attractive from an attacker’s point of view, and the most widely used application isn’t necessarily the one attackers will go after.
About 10% of large enterprises have an Internet-exposed instance of VMware Horizon, a desktop and application…
Source: www.darkreading.com – Read more