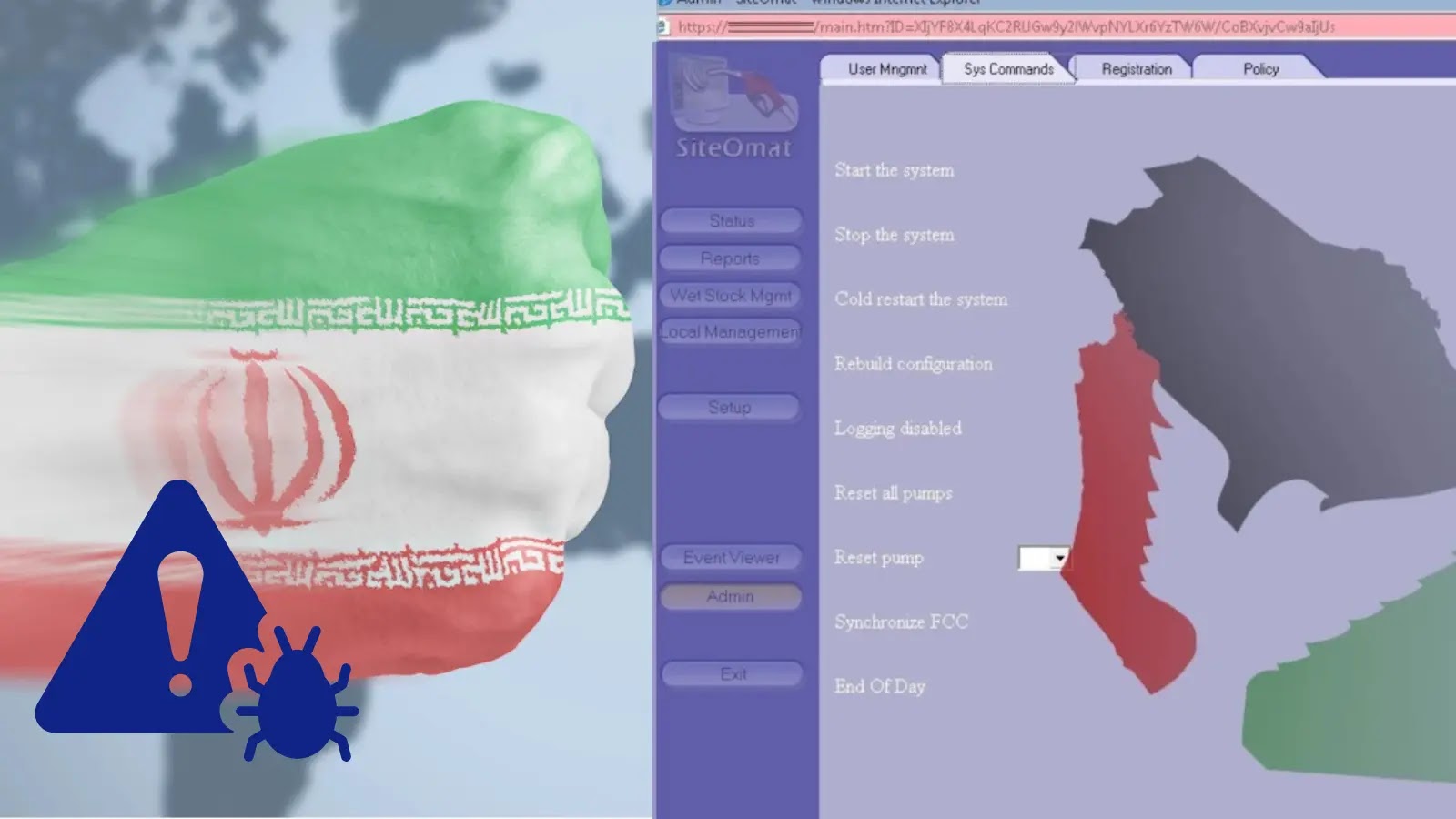
A new malware strain, IOCONTROL, has emerged, threatening Internet of Things (IoT) and operational technology (OT) systems, particularly within critical infrastructure. The malware, allegedly created by the pro-Iranian hacktivist group “Cyber Av3ngers,” allows for remote access, manipulation, and surveillance of infected systems. Organizations are advised to enhance their defenses against evolving threats like IOCONTROL by implementing robust IoT and OT security measures.

What are business logic vulnerabilities?
Business logic vulnerabilities in software allow attackers to exploit flaws in design, enabling them to circumvent security measures and manipulate pricing, authentication, and other key