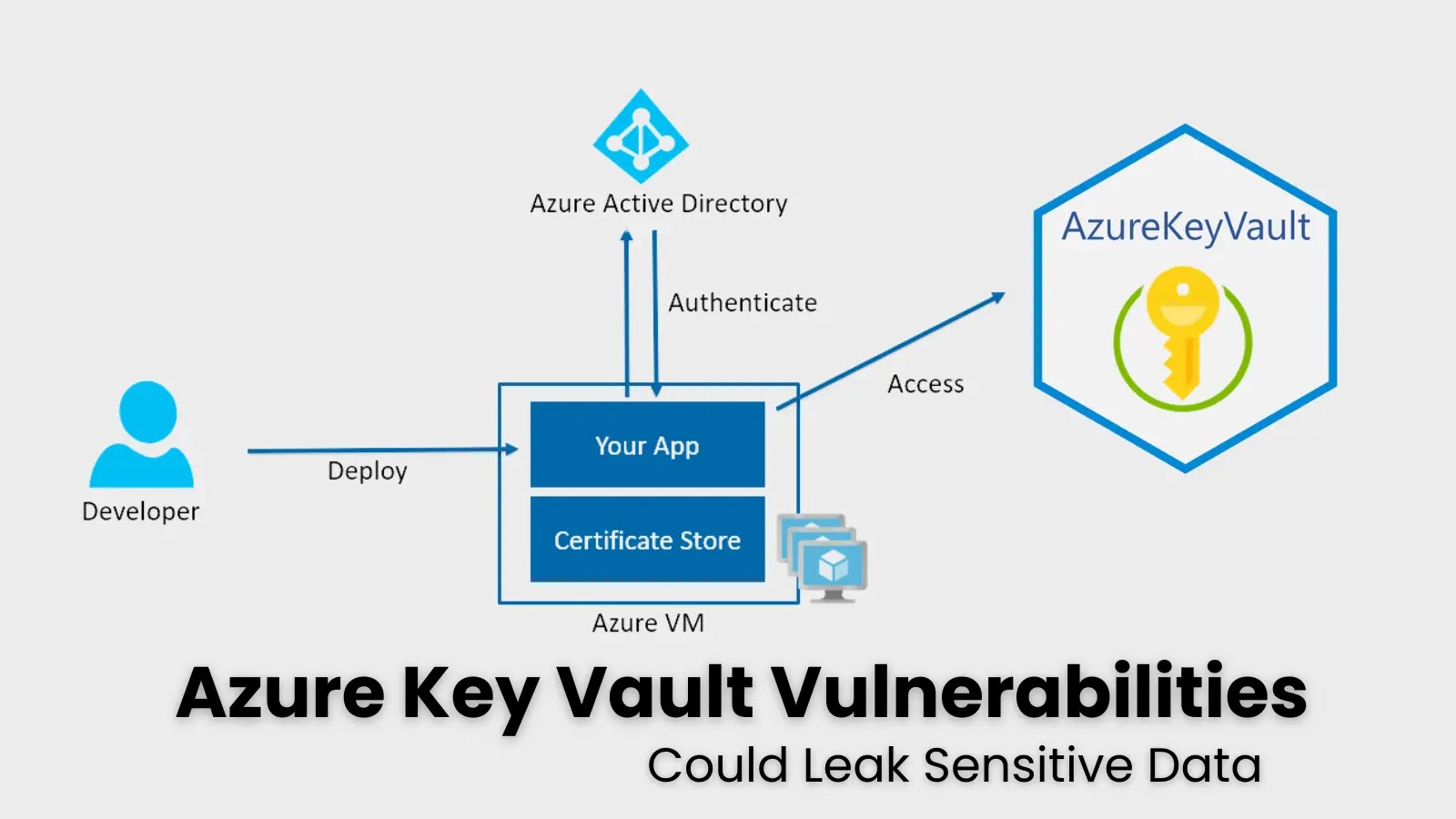
Attackers can exploit Azure Key Vault by manipulating access policies after compromising Entra ID (Azure AD) credentials, as detailed in a penetration testing report. Utilizing PowerShell, Microsoft Graph API, and Burp Suite, attackers enumerate resources, access keys, and decrypt sensitive data. The report emphasizes the importance of robust Role-Based Access Control, auditing logs, and implementing strong security measures to mitigate risks.

Weathering the digital storm: preparing for the inevitable cyber hurricane – Re-Insurance.com
“Preparing for cyber threats is essential in today’s digital world. Organizations must invest in robust cybersecurity measures to weather the inevitable cyber attacks. Stay ahead