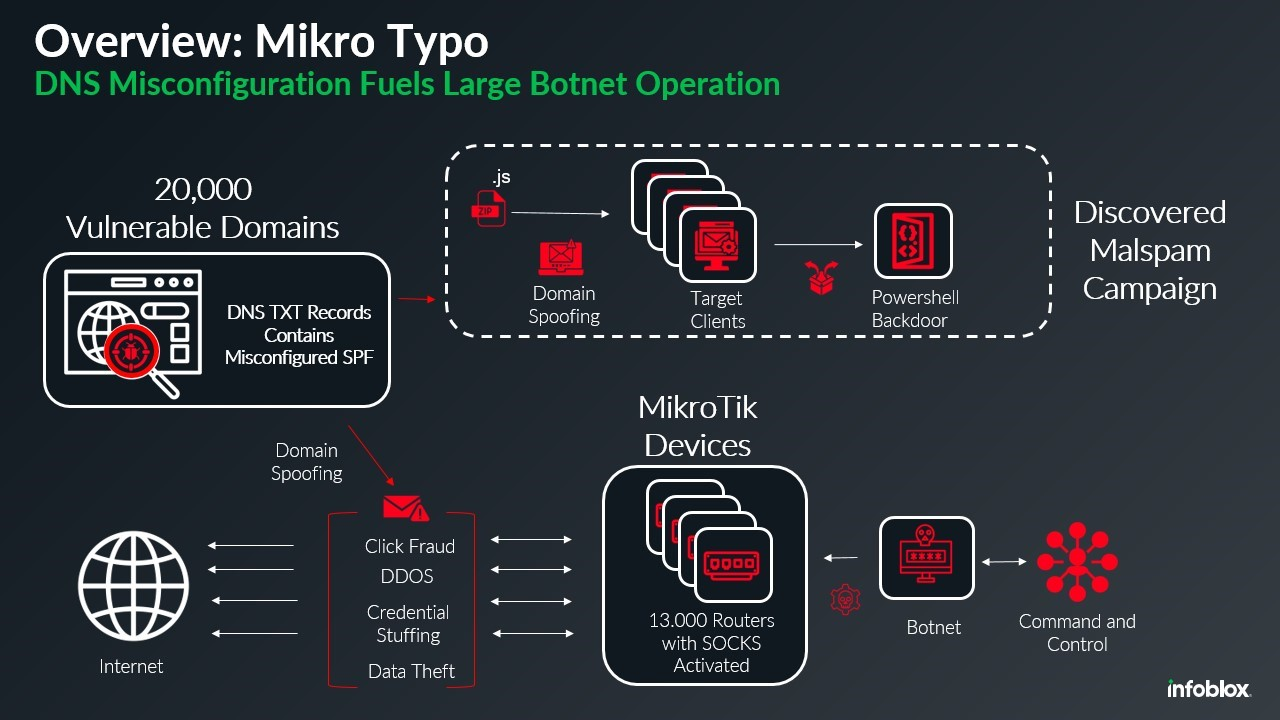
A 13,000-device MikroTik botnet is spreading malware by exploiting DNS misconfigurations. The malware is delivered via spoofing 20,000 domains and bypassing email protections; the botnet employs MikroTik routers to mask malicious traffic origins and boost the scale of its operations. Researchers have also discovered that botnet operators are exploiting improperly configured DNS records to enable any device to spoof legitimate domains in emails.
HHS Office for Civil Rights Reaches $10,000 Settlement over HIPAA Ransomware Cybersecurity Probe – DataBreaches.Net
Alright, let’s have a natter about an interesting development in the realm of healthcare cybersecurity. Recently, a surgical group based in Michigan, namely the Northeast