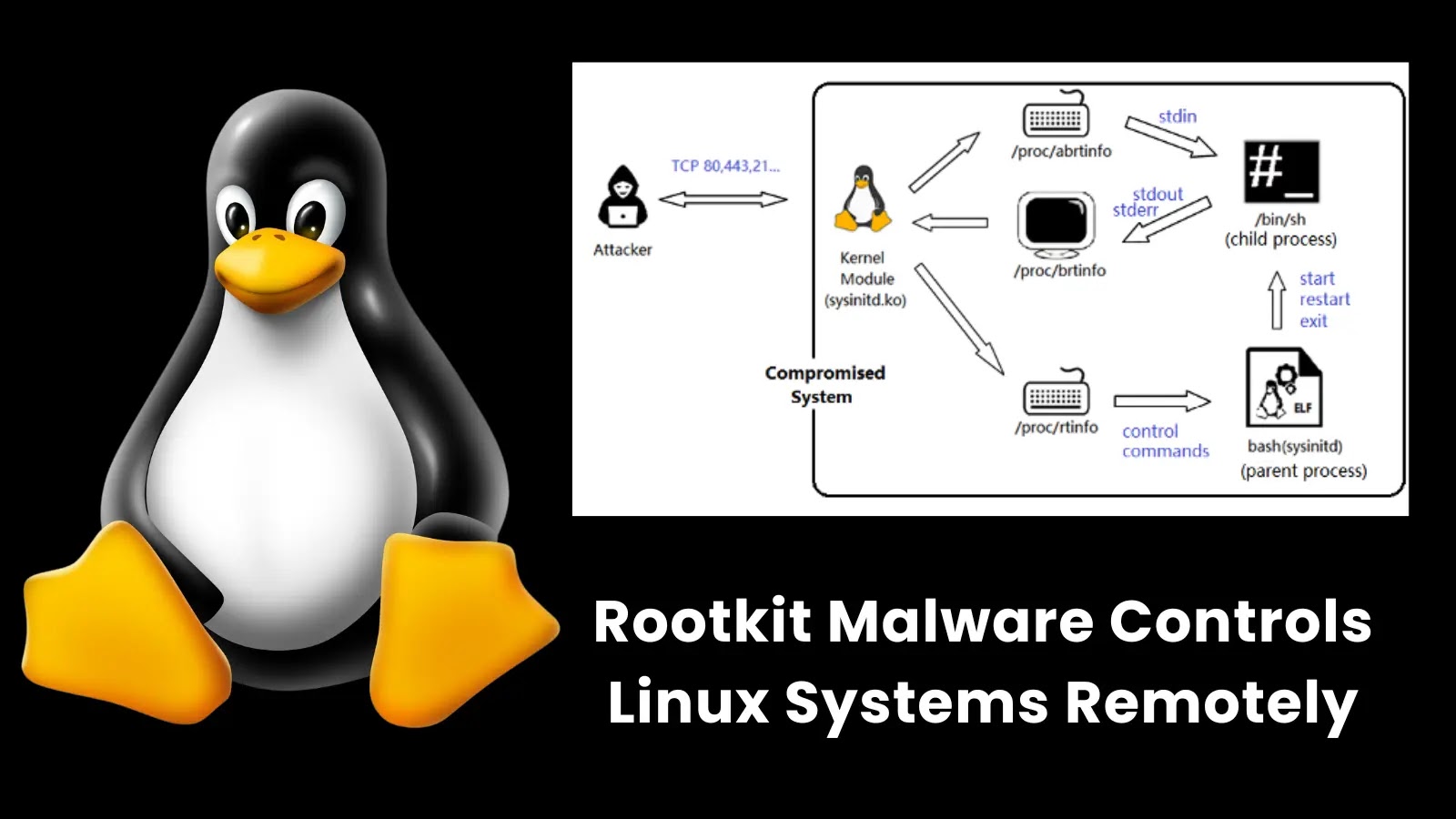
Fortinet has discovered a sophisticated rootkit malware exploiting multiple zero-day flaws in enterprise appliances. The malware uses kernel modules and user-space processes to gain persistence, intercept network traffic, and control compromised Linux-based systems. The malware was embedded in key Linux configuration files to ensure it loaded during system boot. It could execute Linux commands remotely and hijack TCP sessions. Fortinet urged regular updates of systems, monitoring of processes and traffic, and improved security of /proc directory permissions.

North Korean Hackers Use Fake U.S. Companies to Spread Malware in Crypto Industry: Report
North Korean hackers reportedly set up shell companies in the US to penetrate the crypto sector and target developers via fake job offers, according to