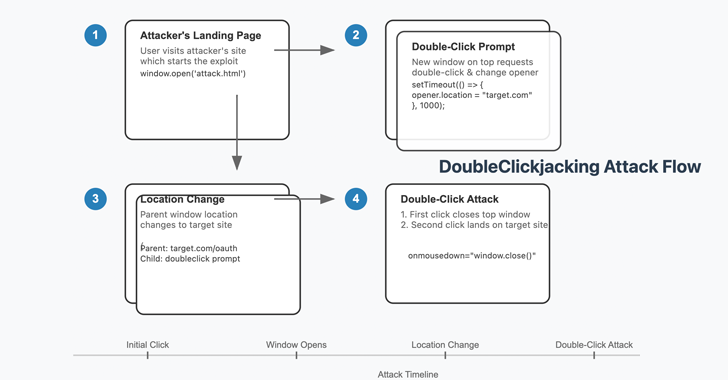
New timing-based vulnerabilities known as DoubleClickjacking, which exploit the gap between the start of a click and the end of the second click, have been discovered. Paulos Yibleo, a security researcher, said these vulnerabilities leverage a double-click sequence that can bypass all known clickjacking protections and facilitate account takeovers on almost all major websites. Preventative measures include disabling critical buttons unless triggered by a mouse gesture or key press, as services like Dropbox already do.

North Korean Hackers Use Fake U.S. Companies to Spread Malware in Crypto Industry: Report
North Korean hackers reportedly set up shell companies in the US to penetrate the crypto sector and target developers via fake job offers, according to