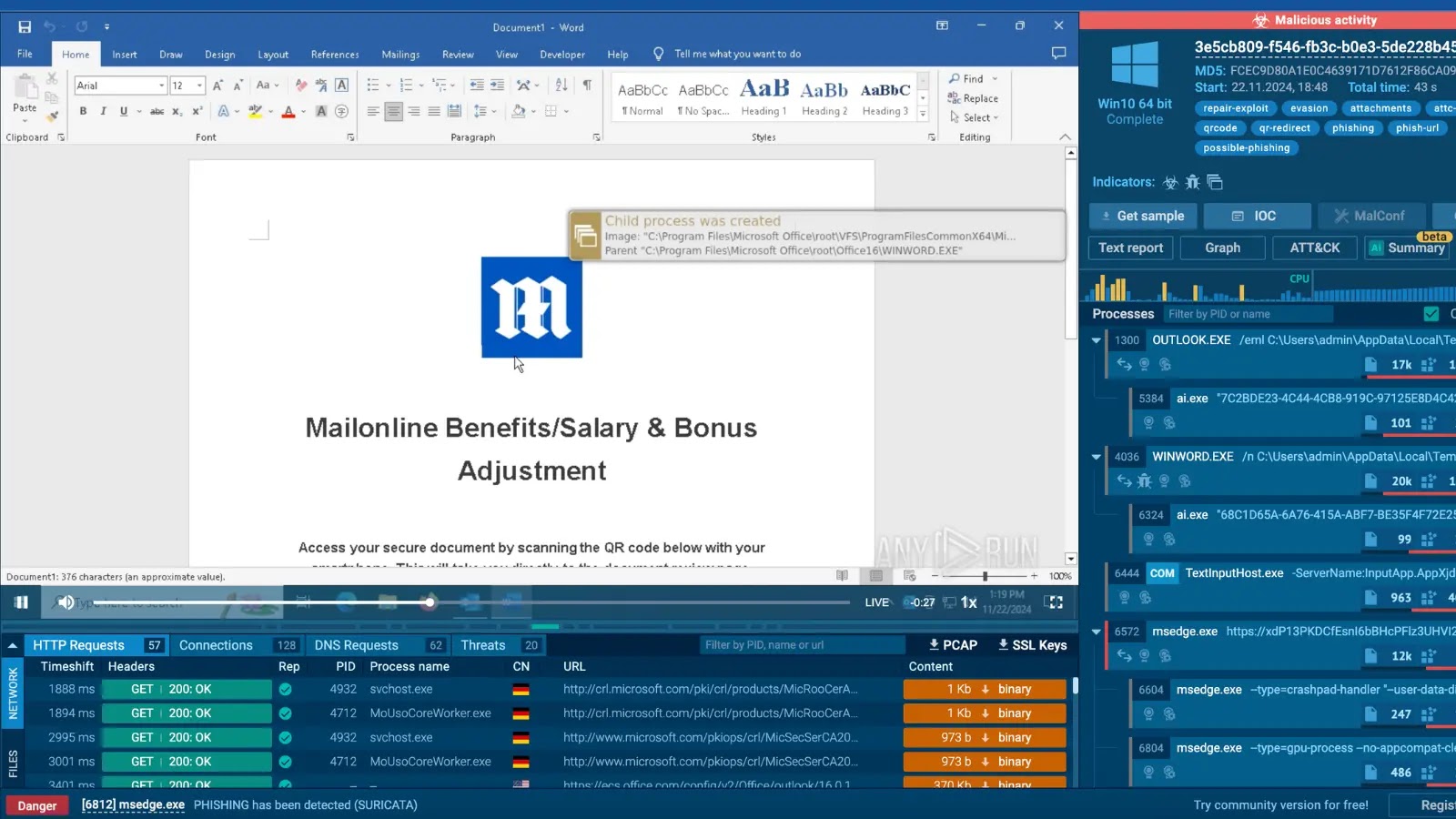
Cybersecurity experts at ANY.RUN have discovered a zero-day attack campaign that uses corrupted files to evade detection by antivirus software and email spam filters. The corrupted files, often appearing like ZIP archives or Microsoft Office documents, execute malicious code when opened. Unlike traditional security tools, ANY.RUN’s interactive sandbox can detect this threat by engaging directly with the files to observe their real-time behaviour.

OIG: OCR should expand scope of HIPAA audit program
The HHS Office of Inspector General (OIG) has called for the Office for Civil Rights (OCR) to expand its HIPAA audit program and define audit