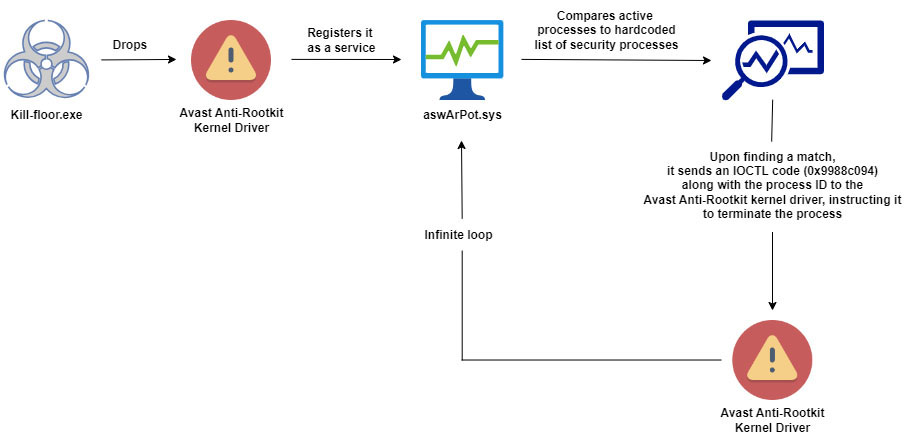
An outdated, vulnerable driver from Avast is being exploited in a sophisticated cyberattack aimed at disabling security measures on targeted systems, according to cybersecurity firm Trellix. The attack uses a “bring-your-own-vulnerable-driver” tactic, allowing attackers to disable 142 security processes from several different vendors. By registering the driver under Avast’s service name using Windows’ Service Control tool, the malware is able to bypass detections and terminate security processes undetected.

Hackers Abuse Avast Anti-Rootkit driver To Evade Detection
A malicious campaign has been discovered where malware, detected as kill-floor.exe, uses the legitimate Avast Anti-Rootkit driver to bypass detection and gain deep access to