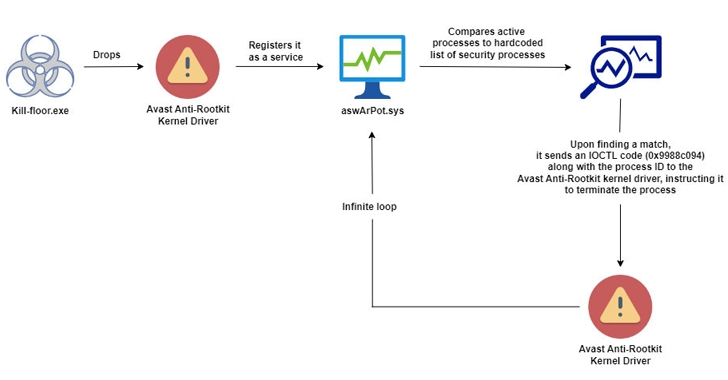
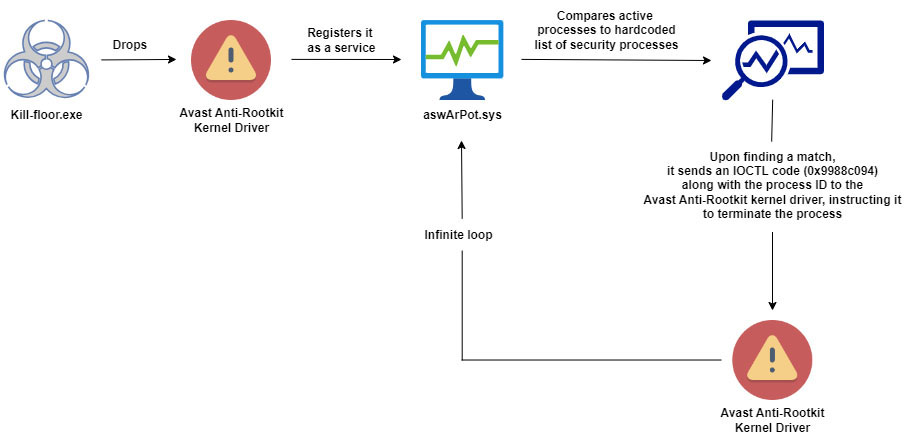
Researchers found a new malware campaign that uses a Bring Your Own Vulnerable Driver (BYOVD) technique. This malware drops a legitimate Avast Anti-Rootkit driver and manipulates it to disable protective software, seize control of the system, and terminate 142 processes, including security software. While the exact access vector and the scope of these attacks aren’t clear, such methods have been widely used to deploy ransomware recently.
Malware campaign abused flawed Avast Anti-Rootkit driver
Threat actors are exploiting a flawed Avast Anti-Rootkit driver to bypass detection, disable security tools and compromise targeted systems, Trellix researchers found. The malware corrupts