Several threat operations have exploited Microsoft’s “ms-appinstaller protocol” to facilitate malware distribution, leading to its deactivation. The intruders were able to bypass safety measures by spoofing legitimate apps, thus installing loader malware and other harmful payloads. Microsoft’s Threat Intelligence team highlighted the use of the protocol for the delivery of the Carbanak malware and BATLOADER.
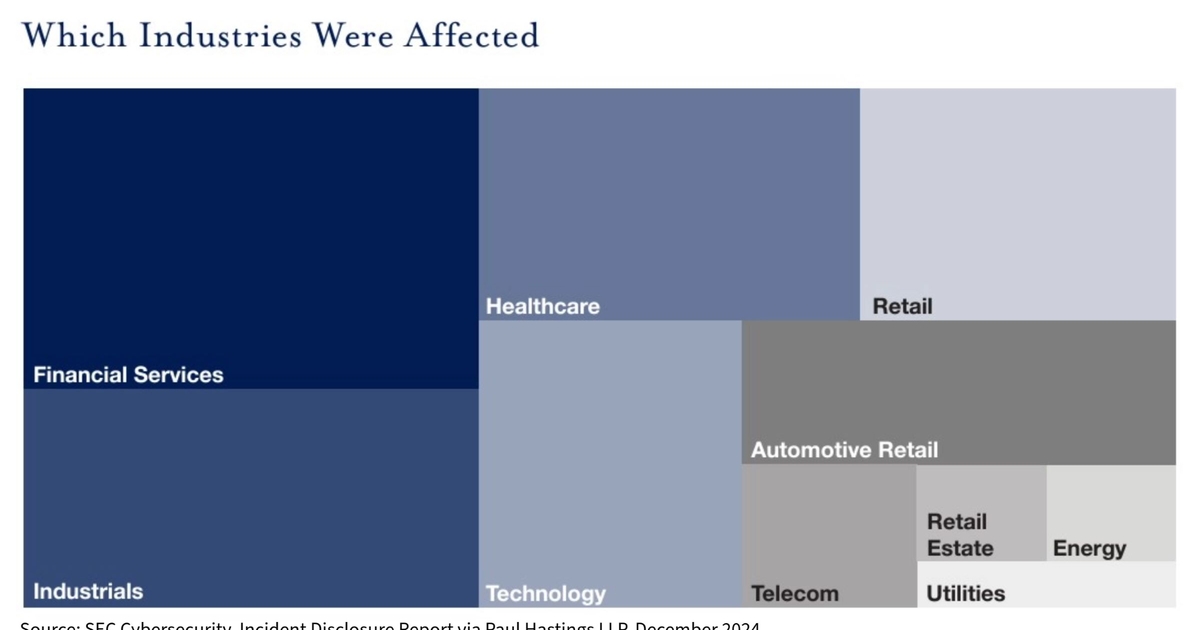
SEC Disclosures Up, But Not Enough Details Provided
New regulations by the US Securities and Exchange Commission (SEC) have caused the number of cybersecurity incident reports from public companies to rise by 60%



