Hardware security solutions like advanced instruction set architecture (ISA) extensions could revolutionize IT security by preventing malicious applications from accessing exploits. Examples include Capability Hardware Enhanced RISC Instructions (CHERI), which controls memory access and retains compatibility with existing software. ISA solutions could protect against memory safety vulnerabilities. The nature of open source technologies allows for collaborations, speeding up progress in the IT and security community.

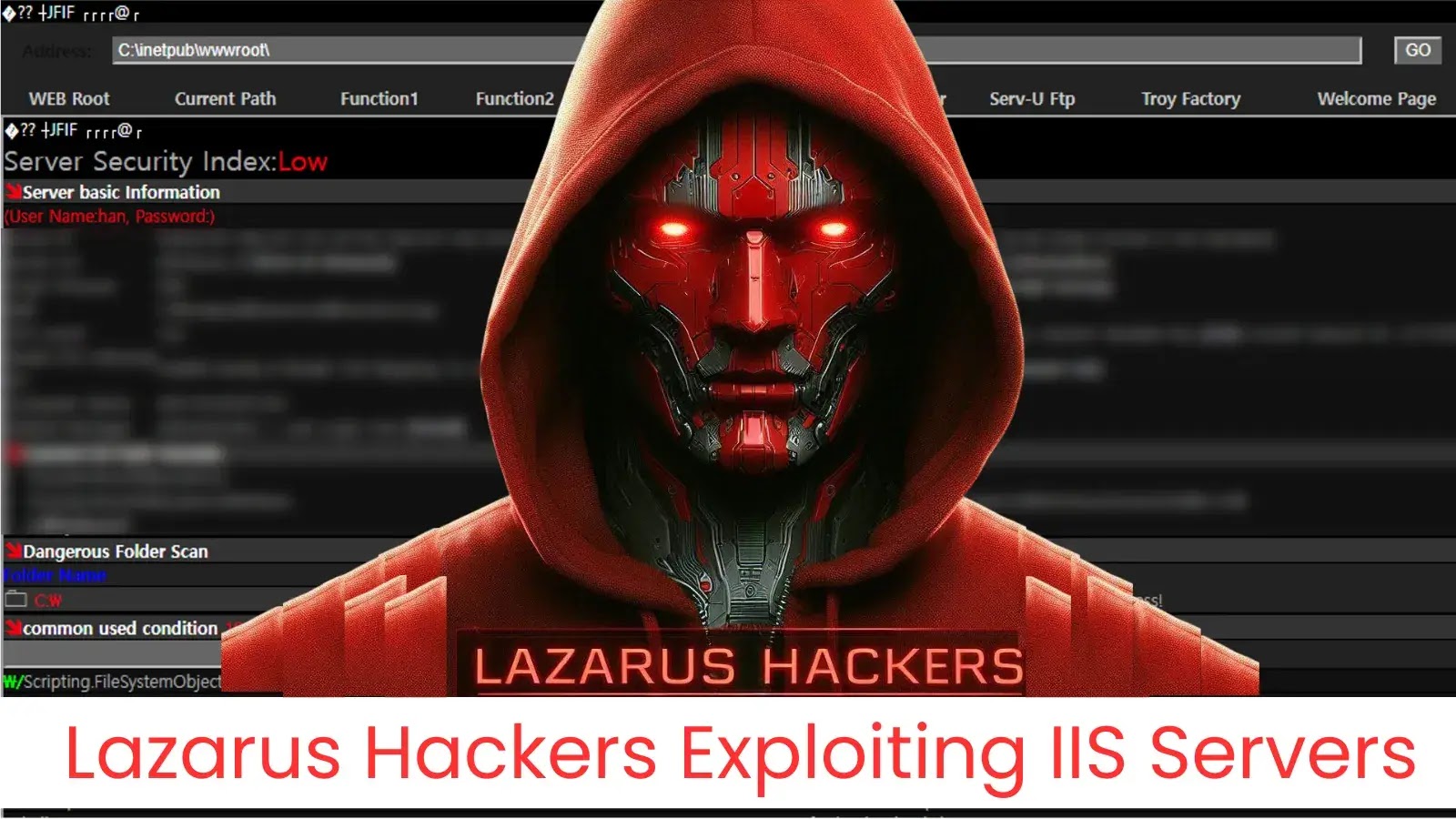
Lazarus Hackers Exploiting IIS Servers to Deploy ASP-based Web Shells
The Lazarus group has launched sophisticated attacks on South Korean web servers, deploying ASP-based web shells as first-stage Command and Control (C2) servers. These attacks,