IBM X-Force has been monitoring the evolution of Russian threat actor Hive0051’s malware capabilities for the past 18 months, noting significant advances. Key improvements include a multi-channel approach to DNS fluxing, obfuscated multi-stage scripts, and fileless PowerShell versions of Gamma malware. Hive0051’s escalating activity, including an increase in active infections and unique malicious domains, signifies an elevation of resources and ongoing operations.

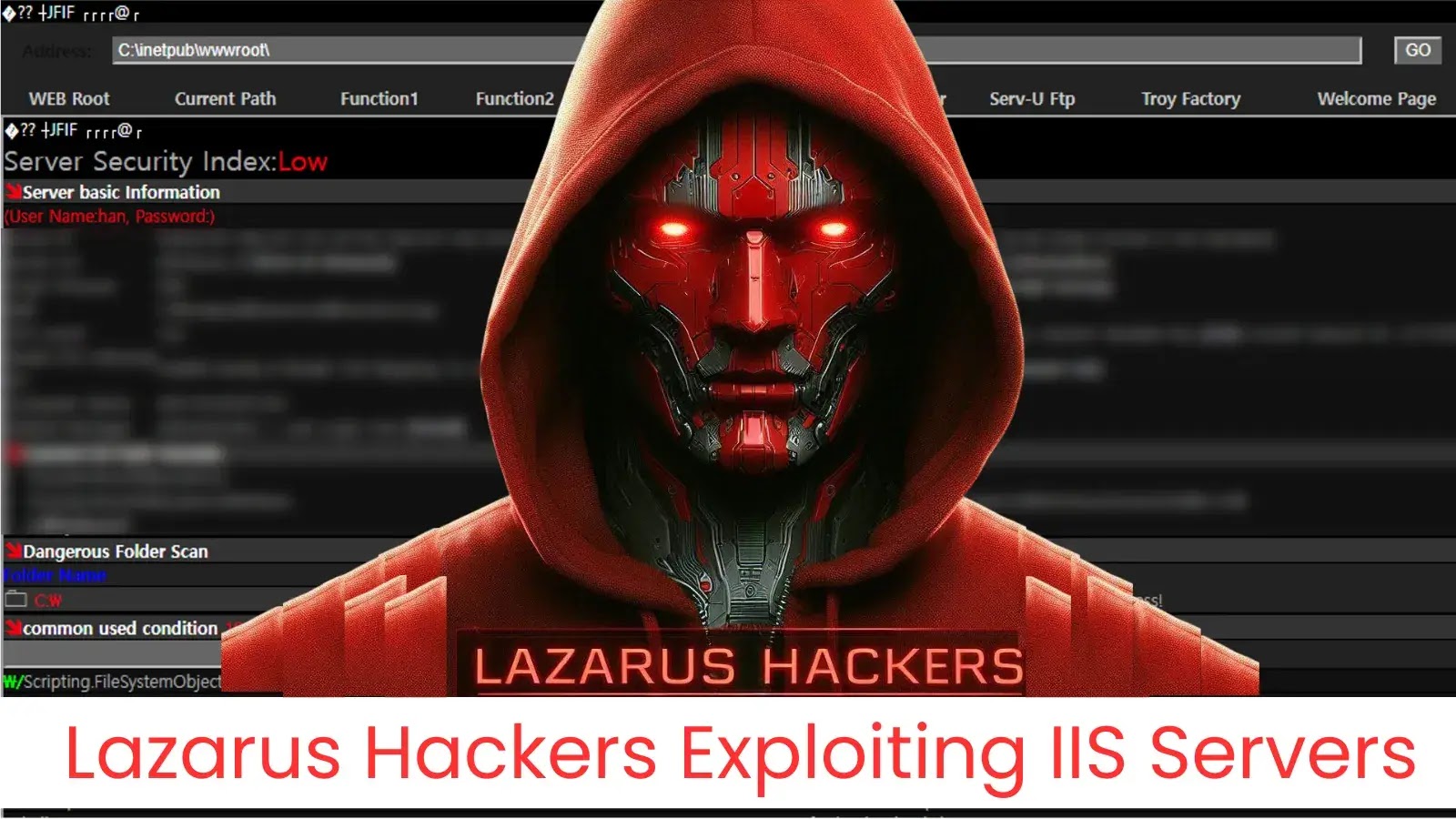
Lazarus Hackers Exploiting IIS Servers to Deploy ASP-based Web Shells
The Lazarus group has launched sophisticated attacks on South Korean web servers, deploying ASP-based web shells as first-stage Command and Control (C2) servers. These attacks,