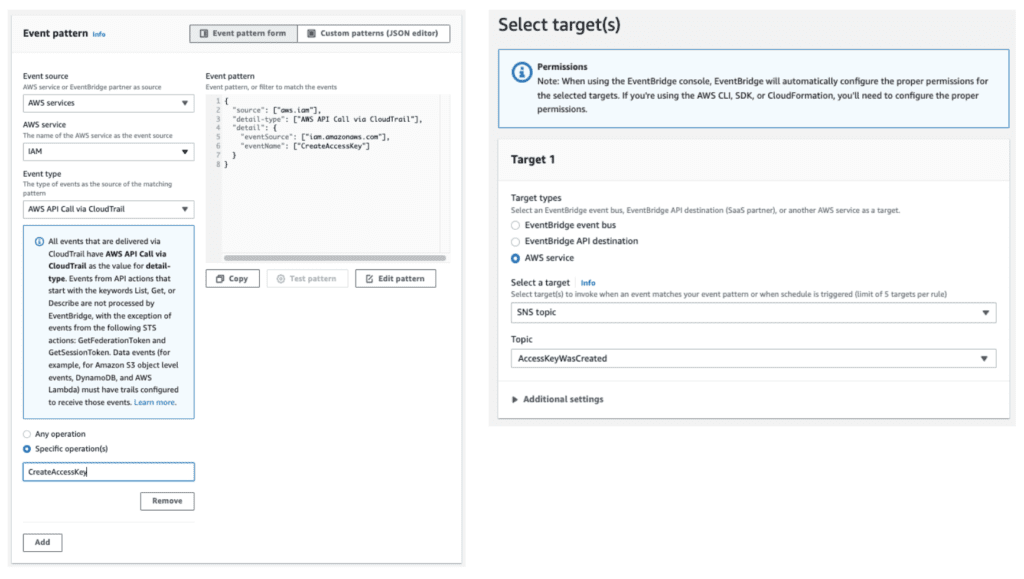
When misused or otherwise not used securely, AWS IAM user access keys have long been one of the most effective, lowest hanging fruits for attackers seeking a foothold in a cloud environment. Such credentials are one of the main culprits in some highly damaging breaches reported in the past few…
Source: securityboulevard.com – Read more

Cybersecurity Industry Gains $1.7 Billion to Develop Cutting-Edge Protection Technologies
In April 2025, cybersecurity startups raised $1.7 billion, signaling a shift to proactive digital defense strategies amid escalating threats. Leading investments, particularly in AI-driven solutions,